|
Malware aimed at uncovering the anonymous identities of Tor users reportedly sent information to an IP address that belongs to the National Security Agency (NSA), routed through Science Applications International Corporation (SAIC).
Tor, an anonymity network originally short for The Onion Router, was developed with contributions from individuals who worked for the Navy and the NSA. This latest revelation comes as the NSA is under increasingly intense scrutiny around the world for their data harvesting activities.
It also comes on the heels of a report stating that the FBI regularly employs hackers to develop malware and an earlier report which stated that the US government is the world’s largest buyer of malware.
The NSA link was uncovered by researchers from Baneki Privacy Labs, a group of Internet security researchers, along with CryptoCloud (plus CriptoStorm.is and CriptoStorm.org), a VPN provider.
The IP address, hardcoded into the JavaScript exploit, was discovered by Cryptocloud but a Baneki source told Ars Technica that they reached out to other researchers in the malware and security community to identify the source.
The exploit specifically targeted FireFox Extended Support Release 17 for Windows, the same browser that was released as a part of the Tor Project’s Tor Browser Bundle.
The vulnerability exploited was patched by Mozilla in June of this year and the patched version is part of the new Browser Bundle.
However, Ars points out that,
Early investigations traced the IP address back to SAIC, which incidentally provides support to the Department of Defense in the areas of information technology and Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance (C4ISR).
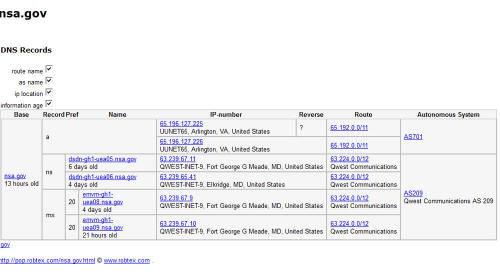
The IP address was specifically tracked to the SAIC facility in Arlington, Virginia, though further analysis turned up that it went beyond the defense contractor.
Research using Robtex, a DNS record tool, found that the IP address was part of one of many blocks of IP addresses which have been permanently assigned to the NSA.
Ars Technica points out that this discovery is one of two things: a laughable mistake by someone working for either the NSA or SAIC, or,
An individual posting on Cryptocloud’s discussion forum speculated,
Kevil Poulsen, writing for Wired’s Threat Level, on the other hand, believes that “the FBI is the prime suspect.”
They note that if Vlad Tsrklevich and others are correct, it could be the FBI’s computer and internet protocol address verifier (CIPAV).
CIPAV is a piece of law enforcement spyware first covered by Wired back in 2007, though it has reportedly been in use since 2002.
SAIC has not responded to attempts by Wired to get a comment on the story, and Poulsen notes that SAIC is a contractor for the FBI.
The discovery of the exploit came soon after the FBI reportedly sought to extradite Eric Eoin Marques, 28-year-old founder of Freedom Host, on child pornography charges.
It also came after individuals involved with the Tor Project reported the disappearance of numerous so-called “hidden service addresses” that were used by Freedom Hosting.
It seems that the evidence indicating that the IP address is linked to the NSA is quite strong, though if that is the case, they almost certainly provided information to the FBI in relation to the Marques case mentioned above.
|