|
from PCWorld Website
You had to see this one coming.
This week, it came to light that a small error in the open-source OpenSSL implementation of the SSL encryption protocol opened a gaping hole in the security of hundreds of thousands websites and networking equipment across the Net - and that hole had been wide open and exploitable for years.
Passwords could be easily grabbed. User names matching those passwords could be easily grabbed. Heck, userdata could be easily grabbed.
The "Heartbleed" moniker attached to the devastating bug seemed all too apt.
And Friday afternoon, Bloomberg reported that the National Security Agency has been aware of and actively exploiting the Heartbleed bug for at least two full years, citing "two people familiar with the matter."
Ironically, the report comes on the same day that the U.S. Department of Homeland Security issued a warning about Heartbleed, stating that,
Nagging NSA concerns
NSA HQ.
The allegations are sure to cause an uproar in the security community, which is still struggling to come to terms with the revelations revealed by whistleblower Edward Snowden.
Leaked NSA documents provided to reporters by Snowden have revealed an agency casting a wide - and often domestic - surveillance dragnet, spying on American emails and web searches, gobbling up metadata from smartphones en masse, and even tapping into the internal communication infrastructures of Internet giants like Yahoo and Google.
A September Snowden-supplied revelation revealed that the NSA can easily defeat many of today's encryption technologies, and in an aside that now seems precognizant, the SSL protocol was then rumored to be a particular favored target for the Agency.
NSA representatives declined to comment to Bloomberg about the report.
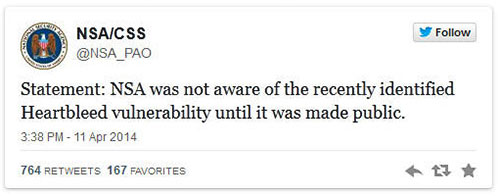
Update:
The NSA's Twitter account just wrote the following:
for Source, click above image
What can you do?
While the security of open-source software has been debated in the wake of Heartbleed's devastation, the Web is already recovering from the bug's widespread mayhem.
There's already an OpenSSL fix for Heartbleed, which many website administrators are scrambling to implement.
Given the nature of the Heartbleed bug - which reveals information stored in a web server's RAM, as wonderfully summed up by XKCD - you actually don't want to change your passwords or even visit sites that were vulnerable, but have yet to be fixed.
Be sure to read PCWorld's comprehensive guide to staying safe from Heartbleed, and check out our coverage of sites known to have been affected by the bug.
- How to Keep Your Private Info Safe
-
No matter how hard you try to stay safe, some aspects of securing your online data are completely out of your hands.
That fact was made painfully obvious on Monday, when the Internet got caught with its collective pants down thanks to a critical vulnerability affecting a fundamental tool for secure online communications.
Called Heartbleed, the bug has been in the wild for more than two years now. It allows attackers to exploit a critical programming flaw in OpenSSL - an open source implementation of the SSL/TLS encryption protocol.
When exploited, the flaw leaks data from a server's memory, which could include SSL site keys, usernames and passwords, and even personal user data such as email, instant messages, and files, according to Finland-based Codenomicon, the security firm that first uncovered Heartbleed in concert with a Google researcher.
That's bad. Real bad, though it's important to note that Heartbleed only affects OpenSSL and not the security protocol itself.
But due to OpenSSL's popularity with website administrators, the potential number of affected websites is huge. Security and Internet research firm Netcraft estimates that Heartbleed affects around half a million "widely trusted websites."
Yahoo has already said it was hit by the Heartbleed bug and Yahoo-owned Tumblr is advising users to update their passwords ASAP.
Yes, this bug is pretty serious and almost certainly affects at least one of your online accounts.
But now that we've got the scary stuff out of the way, let's talk about some of the practical measures you need to know about.
Keep calm and...
Thanks to Hearbleed it's possible that some unscrupulous actors online could have your username and password. And you should definitely change your password on any site that says it was affected.
But here's the thing:
In fact, it could make things worse.
...don't carry on
Heartbleed was publicized on Monday.
So by now, many sites should have scrambled (or are scrambling) to patch their servers. You can find out if a site is still affected by Heartbleed using online checkers provided by LastPass, Qualsys, or Filippo Valsorda.
If you find that a site you use often is still affected by the vulnerability, Codenomicon advises to take a "day off" from that site.
Heartbleed only exposes data that's held in a server's memory (RAM). This isn't a break-in and read the database type flaw. Your data needs to be in a server's memory when it's attacked to be exposed.
That's one reason why changing your password before a site is patched could actually be worse than doing nothing, especially now that Heartbleed is public knowledge.
Other considerations
Security flaws like this are also a good time for some reminders about how best to secure your online accounts.
You should really be using two-factor authentication for all your accounts that offer it. Two-factor authentication requires you to enter an extra code before accessing your online accounts.
The code is typically generated by a smartphone app or keychain dongle, but you can also receive codes to your phone via SMS. This extra step requires attackers to know how to generate your two-factor authentication code before they can login to your account.
In the case of Heartbleed, two-factor authentication may not have been as useful a defense, but in general this extra step helps keep your account safer than it was.
Use a password manager
Now's a good time to start using a password manager especially if you're going to be changing some user logins over the next few days.
A password manager makes it easy to generate randomized passwords using a combination of letters, numbers, and special characters. It also relieves you of having to memorize every one of those overly complex codes.
Password managers often come with other features as well such as secure notes, and autofill for online forms.
There are many options out there for password managers, but some of our favorites include LastPass, Dashlane, and KeePass.
LastPass recently said in a blog post that it was using the version of OpenSSL affected by Heartbleed; however, because the service encrypts your data before transmitting it online, the company says its users were not at risk of having their data exposed to the bad guys.
Heartbleed is certainly a nasty little bug that needs to be taken seriously. But considering it's been in the wild for more than two years, there's not much a user can do now except wait patiently for affected sites to patch their servers before changing any passwords.
Once those sites are patched, however, you'll want to change your password as soon as possible.
Encrypted Communications at Risk
Computer security experts are advising administrators to patch a severe flaw in a software library used by millions of websites to encrypt sensitive communications.
The flaw, nicknamed "Heartbleed," is contained in several versions of OpenSSL, a cryptographic library that enables SSL (Secure Sockets Layer) or TLS (Transport Security Layer) encryption. Most websites use either SSL or TLS, which is indicated in browsers with a padlock symbol.
The flaw, which was introduced in December 2011, has been fixed in OpenSSL 1.0.1g, which was released on Monday.
The vulnerable versions of OpenSSL are 1.0.1 through 1.0.1f with two exceptions: OpenSSL 1.0.0 branch and 0.9.8, according to a special website set up by researchers who found the problem.
If exploited, the flaw could allow attackers to monitor all information passed between a user and a Web service or even decrypt past traffic they've collected.
The bug was discovered by three researchers from Codenomicon, a computer security company, and Neel Mehta, who works on security for Google. The scope of the problem is vast, as many modern operating systems are suspected as having an affected OpenSSL version.
Operating systems that may have a vulnerable version of OpenSSL include,
...they wrote.
The "oldstable" versions of Debian Squeeze and Suse Linux Enterprise Server are not vulnerable.
OpenSSL also underpins two of the most widely used Web servers, Apache and nginx. The code library is also used to protect email servers, chat servers, virtual private networks and other networking appliances, they wrote.
The problem, CVE-2014-0160, is a missing bounds check in the handling of the TLS heartbeat extension, which can then be used to view 64K of memory on a connected server, according to another advisory.
It allows attackers to obtain the private keys used to encrypt traffic. With those keys, it is also possible for attackers to decrypt traffic they've collected in the past.
The attackers can only access 64K of memory during one iteration of the attack, but the attackers can "keep reconnecting or during an active TLS connection keep requesting arbitrary number of 64 kilobyte chunks of memory content until enough secrets are revealed," according to the website.
It's unclear if attackers have been exploiting the flaw over the last two years, which was just publicly revealed on Monday. But attacks using the flaw "leaves no traces of anything abnormal happening to the logs," the researchers wrote.
Administrators are advised to apply the up-to-date version of SSL, revoke any compromised keys and reissue new keys.
|