|
While the sources for the article are anonymous, they hardly need naming since Schneier makes it clear that his research has collected insight from virtually all major internet companies, from large service providers like AT&T all the way to organizing bodies like Verisign or potentially even ICANN itself.
Somebody is searching for weaknesses in the sorts of places that many assume you'd only attack for one reason:
The basic narrative is this:
These have been not only getting stronger, longer lasting, and more diverse, but they've been moving in seemingly systematic, investigatory ways.
Schneier describes a scenario in which
attackers sent predictable probing attacks against successively
higher levels of security until it had tested everything, apparently
being exhaustive in their search for failure points.
One important aspect of these attacks is their power and frequency, implying enormous resources at the disposal of the attacker and strongly indicating a nation-state as the culprit.
Schneier name-drops both China
and Russia as the most likely culprits (China most of all),
but he can't say for sure. In addition to the sheer volume of the
attacks, however, is their variety, forcing defenders to roll out
their full complement of defenses. This could be interpreted as an attempt to get defenders to "bare all," and make their full defensive capabilities known.
Corero director Sean Newman said the attacks his company has seen are short and "sub-saturating," likely meant to slowly approach and find the target's exact maximum traffic capacity.
More worrying, the attacks also seemed to be interested in the response procedures of these bodies, like the ability to change addresses and routes in response to attacks.
These incursions, more than anything else, seem to imply that the attacker is thinking through the possibility of really attacking someday. They're looking at not only the points of ingress, but the response times, and points of egress - everything you'd need to know to attack and get away with it.
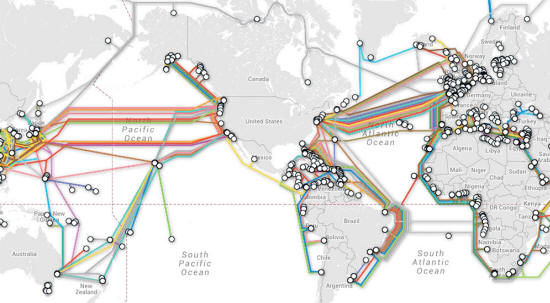
The "internet backbone" is a more real, physical thing than people often imagine.
Accepting all of Schneier's intelligence as genuine (and it almost certainly is), we still have to note here the inherent assumption in his thinking:
It's a fairly safe assumption, but one that does overlook the possibility that this could be the product of a very understandable paranoia on the part of other world powers.
As Schneier himself points out, the NSA has more investigatory hardware on the internet backbone than all other powers combined, so it can't be surprising that the internet is seen as an inherently American, culturally aggressive thing.
Investigating such a system could at least tell you how best to route your diplomatic cables to avoid being hoovered up by NATO listening hardware.
Russian ships perform "tactical exercises" over the deep sea internet backbone.
The other very real possibility is that these attacks were meant to be seen, and meant to be publicly known.
Much like alleged Russian hacking of political documents, a basic point is being made about the abilities that can be arrayed against the United States… should that kind of action become necessary.
The implicit threat is not so different from making sure your adversary sees you install a missile battery within range of their border.
You're saying something, very clearly: Watch your ass.
The seeming flaw in this explanation, of course, is that the real attacks most feared to follow these reported investigatory probes may be too indiscriminate to be an effective threat against any one actor, even the US.
This means that if it is a threat, it's a threat against everybody.
Much like Russian threats against the physical internet backbone in the deep sea, it's believed that any major attack would have to coincide with a major reorientation of the attacking society away from the online space, or it would end up being suicide - it's just a shame that such reorientation efforts are well under way.
The Russian government seems to be looking into the feasibility of making do with a Russian-bloc-only intranet with only semi-porous connections to the larger online world.
If it did manage to implement such a system, cutting off the global internet would be far less harmful to their own interests. In China the process is even further along, as the country continues to pioneer frankly incredible technologies and procedures to further lock down the internet.
What has once been dismissed as a fool's errand is now a reality:
The idea is classically that the global internet is so important to everyone that nobody but ISIS and maybe North Korea could consider crippling or destroying it - but both China and Russia are expending real effort to at least explore such a possibility.
It's a far-out threat, one that could conceivably start a major global war if done in certain provocative ways, and so it's probably mostly meant as a threat.
The message could be broadly similar to that delivered by a nuclear test:
Why is this made out of anonymous quotes? Why aren't companies willing to talk about the very real threats to their security?
We have to assume the national security world is more aware of this than Schneier is, as the article's final line is telling:
|