|
American Behavioral Scientist from LEGE Website
This may explain why, until recently, social scientists have focused, instead, on graft, bribery, embezzlement, and other forms of government corruption where the aim is personal enrichment rather than social control, partisan advantage, or political power. In any event, the topic is sensitive because it raises questions about the ethics of top leaders and suggests that American democracy may be in thrall to behind-the-scenes manipulations.
Even if research on the issue were to discredit
various conspiracy theories, it could fuel mass cynicism and undermine
civility in public discourse simply by making conspiracy theories a
legitimate subject for public consideration. McCarthyism quite clearly
demonstrated the dangers posed to democracy by unbridled, runaway
accusations of conspiratorial suspicions.
The congressional hearings on Watergate, the Church Committee’s discoveries about illegal domestic surveillance, and the special prosecutors’ investigations of Oliver North and Scooter Libby revealed that public officials at the highest levels of American government can and sometimes do engage in conspiracies to manipulate elections, wiretap and smear critics, mislead Congress and the public, and in other ways subvert popular sovereignty.
Certainly, such crimes and the criminogenic circumstances surrounding them warrant scientific inquiry, not only to better understand elite politics but also to identify institutional vulnerabilities so that protections can be established or strengthened.
The
challenge for scholars is to engage in serious, unblinkered study of the
subject without contributing to mass paranoia or elite incivility.
This article examines the conceptual foundations, political context, and practical implications of research on state crimes against democracy (SCADs).
The SCAD construct is designed to move beyond
the debilitating, slipshod, and scattershot speculation of conspiracy
theories by focusing inquiry on patterns in elite political criminality that
reveal systemic weaknesses, institutional rivalries, and illicit networks.
By definition, SCADs differ from other forms of
political criminality in their potential to subvert political institutions
and entire governments or branches of government. They are high crimes that
attack democracy itself.
Examples of SCADs that have been officially proven include,
Many other political crimes in which involvement by high officials is suspected have gone uninvestigated or unpunished.
Examples of suspected SCADs include,
Considered as a label, the phrase conspiracy theory does a poor job of characterizing speculations about political intrigue, yet the label remains popular because it functions normatively to protect political elites from mass doubts about their motives and tactics (see Manwell, 2010). Although not immediately apparent, this function becomes evident when the label’s surface meaning is compared to its meaning in use.
On the surface, the term conspiracy theory
refers to a suspicion that some troubling event was the result of a secret
plot, but the term’s usage implies something else.
Conspiracy theories of 9/11 claim more than that the attacks were secretly planned and executed by an organized team.
Most conspiracy theories of 9/11 allege that the
U.S. government itself carried out the attacks or that officials knew the
attacks were coming and allowed them to succeed (see, e.g., Griffin, 2004;
Hufschmid, 2002; Marrs, 2006).
Today’s most popular conspiracy theories involve,
Conspiracy theorists argue that official
accounts of these events ignore important evidence, contain anomalies and
inconsistencies, and are tendentious in their exoneration of public
officials
Rather, the broad-brush “conspiracy theory” disparages inquiry and questioning that challenge official accounts of troubling political events in which public officials themselves may have had a hand.
Deployed in public discourse to discredit and
silence those who express suspicions of elite criminality, the label
functions, rhetorically, to shield political elites from public
interrogation.
The label provides no basis for distinguishing
groundless smears from reasonable suspicions warranting investigation.
History has shown all too clearly that public trust in high officials is
sometimes misplaced.
In contrast, the conspiracy theory label is applied not to categorize a position that will actually be considered but to shut off argumentation before it begins.
As a practical matter, the label condemns as
hysterical and pernicious almost all speculations about the possible
complicity of political elites in suspicions events.
George Wallace suspected, with good reason, that the attempt on his life during the 1972 presidential campaign had been engineered by Richard Nixon (Summers, 2000, pp. 406, 473, 526).
Wallace never expressed this suspicion publicly, but this is why he withdrew his support from Nixon during the Watergate hearings.
Similarly, by 1968, Robert Kennedy was convinced that JFK’s assassination had been the work of a conspiracy involving the CIA, but he did not voice his suspicions publicly while running for president because he feared it would discredit him politically or get him killed (Douglass, 2008; Talbot, 2007).
Hence, a useful axiom for scholarly
consideration may conjecture that norms against conspiratorial speculations
in public discourse sacrifice the safety of individual political elites to
protect the legitimacy of political elites as a class.
In the post-WWII era, official investigations have attributed assassinations, election fiascos, defense failures, and other suspicious events to such unpredictable, idiosyncratic forces as lone gunmen, antiquated voting equipment, bureaucratic bumbling, and innocent mistakes, all of which suspend numerous and accumulating qui bono questions.
In effect, political elites have answered
conspiracy theories with coincidence theories.
The research has discredited official accounts of many incidents, thus casting suspicion on the government.
But such ad hoc research has failed to actually
solve the crimes under analysis or even to identify the agencies and
officials most likely to have been the perpetrators.
Similar to research on white-collar crime, domestic violence, serial murder, and other crime categories, SCAD research seeks to identify patterns in SCAD victims, tactics, timing, those who benefit, and other SCAD characteristics.
These patterns offer clues about the motives,
institutional location, skills, and resources of SCAD perpetrators. In turn,
as SCAD research brings SCAD perpetrators into focus, it provides a basis
for understanding and mitigating the criminogenic circumstances in which
SCADs arise.
Public officials are usually quite reluctant to allow independent investigations into questions about their own actions or those of their close associates.
For over a year after 9/11, the Bush-Cheney administration resisted and dodged demands for a 9/11 Commission before finally acceding to pressures from the victims’ families, at which point the administration gave the commission a very small budget and placed it under unrealistic deadlines (Shenon, 2008, pp. 25, 29-31, 36-38).
The crimes for which Richard Nixon was forced from office were not the Watergate break-ins but his efforts to obstruct the FBI’s investigation.
Nixon also tried to preempt congressional
inquiries by issuing a superficial study from the White House (Kutler, 1997,
pp. 239), as did Ronald Reagan when the Iran-Contra scandal first surfaced
in the media (Hinson, 2010).
Also, a key member of the Warren Commission was Allen Dulles, the former head of the Central Intelligence Agency whom Kennedy had fired after the Bay of Pigs.
The 9/11 Commission was similarly compromised (Griffin, 2005; Shenon, 2008). All of its members were government insiders, and none was a vocal critic of the Bush administration.
Moreover, the Commission’s executive director, Philip Zelikow, had previously served on George W. Bush’s presidential transition team, had been appointed by Bush to the president’s Foreign Intelligence Advisory Board, and had drafted America’s national security strategy following the events of 9/11 (Shenon, 2008, pp. 43-44).
Both the commission’s chair and its executive
director had to recuse themselves from parts of the inquiry because of
'conflicts of interest' (Shenon, 2008, p. 171).
Both the FBI and the CIA concealed evidence of their contacts with Lee Harvey Oswald and Jack Ruby (Douglass, 2008, pp. 40-41, 65-66, 144-145, 333-334, 363-368; Talbot, 2007).
Likewise, the Department of Defense appears to
have withheld from the 9/11 Commission evidence that military intelligence
agents had uncovered the 9/11 hijackers’ activities well in advance of
September 2001 (Ahmed, 2005; C. Weldon, 2005).
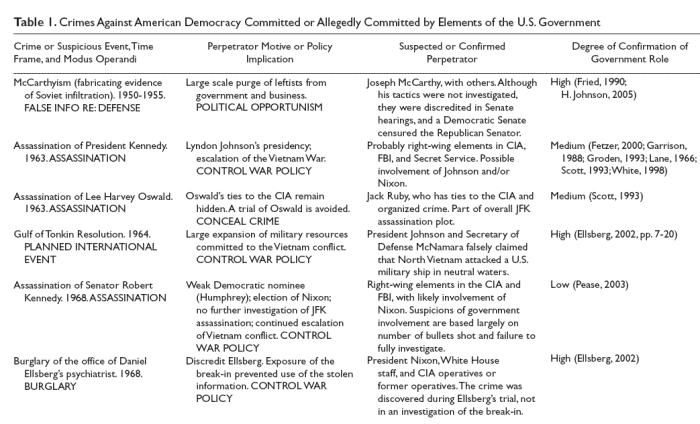
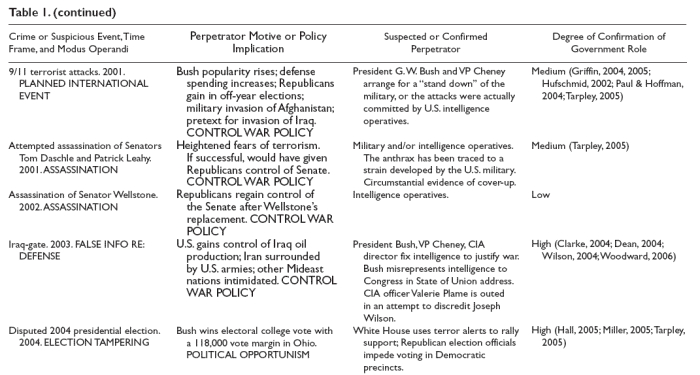
Table 1 contains a list of 15 known SCADs and other counter-democratic crimes, tragedies, and suspicious incidents for which strong evidence of U.S. government involvement has been uncovered.
For each SCAD or alleged SCAD in the list, the table includes a brief description of,
In the list of SCADs in Table 1, several patterns stand out.
Assassinations
Several patterns contradict the conclusion from official inquiries that political assassinations in the United States have been random, with no connections to one another and no involvement of political elites. First, the range of officials targeted for assassination is limited to those most directly associated with foreign policy: presidents and senators.
Most other high-ranking officials in the federal government have seldom been murdered, even though many have attracted widespread hostility and opposition.
No vice presidents have been assassinated, nor have any members of the U.S. House of Representatives or the U.S. Supreme Court. If lone gunmen have been roaming the country in search of political victims, it is difficult to understand why they have not struck more widely, especially given that most officials receive no Secret Service protection.
Why did no assassins go after Joe McCarthy when
he became notorious for his accusations about communists, or Earle Warren
after the Supreme Court’s decisions requiring school desegregation, or Spiro
Agnew after he attacked the motives of antiwar protestors, or Janet Reno
after she authorized the FBI’s raid on the Branch Davidians in Waco?
Presidents and senators have been targeted only when their elimination would benefit military and pro-war interests. Because a president who is killed or dies in office is automatically succeeded by the vice president, a presidential assassination would benefit military interests only if the vice president’s background or policy positions were dramatically better for the military than the president’s.
This situation has existed only twice since 1960 - during the presidencies of John F. Kennedy and Ronald Reagan.
Unlike Kennedy, who was trying to end the cold
war, Lyndon Johnson was a well-known hawk and pentagon supporter. Similarly,
although Reagan and George H. W. Bush had similar positions on the cold war,
Bush’s background as former director of the CIA gave him much closer ties
than Reagan to the military establishment.
The Senate is more important to foreign policy than the House because it must confirm cabinet appointments and approve international treaties. However, the death of a single U.S. senator would almost never cause significant shifts in military action or defense policy because individual senators are seldom that powerful.
Hence, if the aim were to affect foreign policy, a senator would be targeted for assassination only in rare instances. This has indeed been the case.
Just one senator is known to have been assassinated since 1960, despite the large number of available targets and the absence of bodyguards. Senator Robert F. Kennedy was murdered after he had denounced the Vietnam War and had become the Democratic Party’s frontrunner for the 1968 presidential nomination.
Given the high probability that RFK would have
been elected, his murder was, in effect, a preemptive assassination of a
president-to-be.
Five months later, on October 9, 2001, letters laced with anthrax were used in an unsuccessful attempt to assassinate two leading Senate Democrats, Majority Leader Tom Daschle and Judiciary Committee Chairman Patrick Leahy.
The anthrax in the letters came from what is known as the “Ames strain,” which was developed and distributed to biomedical research laboratories by the U.S. Army (Tarpley, 2005, pp. 311-318).
Thus, aside from the assassination of Robert Kennedy, the only
other time since WWII that senators have been targeted for death was when a
war was about to be fought for dubious reasons and the death of a single
senator could shift control of the Senate to the political party pushing for
war.1
Conditions conducive to SCADs include periods of warfare or heightened international tensions, administrations with prowar vice presidents, and Senates closely divided along partisan lines. SCADs often appear where presidential politics and foreign policy intersect.
This policy locus could mean that the nation’s
civilian leadership is being targeted by military and intelligence elites or
that military and intelligence assets and capabilities are being politicized
by the civilian leadership, or both.
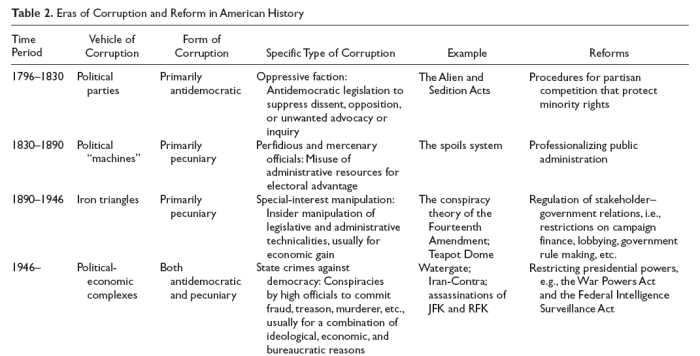
In modern representative democracy, political corruption has taken two principal forms (Rogow & Lasswell, 1963).
Examples here include election tampering, assassination, malicious prosecution, voter disenfranchisement, and unlawful incarceration.
These forms of corruption are not mutually exclusive, but
they are sufficiently distinct to permit analysis of corrupt behavior in
terms of its origins and aims.
Pecuniary corruption, or what the Constitution’s framers referred to as “perfidious” and “mercenary” public officials, was to be impeded by elections (Federalist 28, 57), loyalty oaths (Federalist 29, 44), and the threat of impeachment (Federalist 38, 47, 64, 65 66, 77, 84).
Antidemocratic corruption, which the framers
described as “oppressive factions,” was to be impeded by federalism, divided
powers, and checks and balances (Federalist 9, 11, 47, 51). In the
Constitution, both forms of corruption are captured by the term high crimes
and misdemeanors (Federalist 69).
The main eras of corruption and subsequent reform are listed and described in Table 2 below.
Because reforms have never been totally effective, vulnerabilities from earlier eras continue to be problematic even though they have been mitigated. In this sense, the form and scope of political corruption have expanded over time. SCADs are a new or more sophisticated type of corruption that combines antidemocratic and pecuniary motives of an extreme nature.
SCADs have yet to be adequately targeted for
detection and prevention, although some limited reforms were instituted
after Watergate and Iran-Contra (see Hinson, 2010).
Political Parties
Alliances could be formed between officials in the different offices and branches of government to undercut the system of checks and balances.
Once an enduring alliance of legislative, executive,
and/or judicial powers was in place, many procedural limits on oppressive
majorities would be deactivated, and public officials who represented the
dominant faction could then employ the coercive organs of government to
suppress opponents, conceal information, and in other ways handicap the
electorate’s ability to hold representatives accountable.
As George Washington pointed out in his farewell address, such parties not only weaken the system of checks and balances by placing the reins of legislative, executive, and/or judicial powers in the hands of a single group but also tend, by their very nature, to inspire a certain “team spirit” that blurs the distinctions among legitimate political action, unprincipled political tactics, and political criminality.
This became apparent soon after the first national political party, the Federalists, was organized and gained control of the legislative and executive branches in the election of 1796.
The Federalists enacted the Alien and Sedition
Acts, which ignored the Constitution’s guarantees of free speech and made it
a crime to criticize public officials.
Over the next several decades, the parties developed rules and procedures to regulate the majority and protect the minority’s ability to be heard.
Although partisan competition did not restore
the full vigor of checks and balances to the constitutional system, it did
prevent any majority, oppressive or otherwise, from permanently evading
electoral accountability.
Rather, it drove factions to search for indirect routes to the same end. Officials in the executive branch of government at all levels began to use the powers of their offices to entrench themselves and their parties throughout the political system.
Their main objective was to capture and distribute government jobs and other resources.
Political machines proliferated until, toward
the end of the 19th century, public administration scholars and
practitioners professionalized American government by instituting
professional civil service requirements, prohibiting the use of government
resources in political campaigns, and moving to the council-manager system
in local government.
By creating what became in effect self-contained mini-governments, such commissions opened the door to a cartelization of the political system, whereby public power and resources were divvied up and distributed to various economic, social, and geographic constituencies (Lowi, 1969).
This pattern was repeated with the vast expansion of federal grants in aid to states and localities under the New Deal and the Great Society. Policy making and administration were fragmented into a plethora of separate and distinct arenas where public and private “stakeholders” could work out mutually acceptable compromises more or less independent of the larger political process.
The resulting political-economic conglomerates
have been described variously as “iron triangles,” “whirlpools,”
“subsystems,” and “subgovernments” (deHaven-Smith & Van Horn, 1984; McCool,
1998).
Frequently, the stakeholders in question were corporations and industrial interests - especially railroads, electric utilities, and oil companies - that were suspected of bribing, hoodwinking, or otherwise influencing policy makers to gain legal and financial advantages at the public’s expense.
The earliest example of a suspected manipulation of this sort was described by Charles and Mary Beard (1927) in their “conspiracy theory of the Fourteenth Amendment.” (This, incidentally, is where the term “conspiracy theory” originated.)
According to Beard, legal experts for the railroad industry pushed for and obtained wording that led the courts to apply the legal guarantees of the Fourteenth Amendment not only to individual citizens but also to corporations (Beard & Beard, 1927, pp. 111-114).
Eventually, concerns about the growing potential
for these kinds of special-interest abuses in America’s increasingly
fragmented and technical system of government were addressed with
restrictions on campaign contributions and lobbying, financial disclosure
requirements for public officials, public records and open meeting laws, and
other reforms to reduce improper influences in policy making and
administration.
For the first half of the 20th century, American government’s increasing fragmentation was seen by scholars and practitioners as a positive development that allowed popular participation in policy making while at the same time preventing majority tyranny (see, e.g., Dahl & Lindblom, 1946).
The assumption was that oppressive factions could not exert control over the government as a whole because power, although less well divided in terms of function (legislation, execution, adjudication) than it had been before independent commissions and grants in aid, was now splintered into numerous substantive domains or topics.
In keeping with James Madison’s theory of
faction, with each policy arena dominated by different factions, no faction
or combination of factions would be able to control the government as a
whole, and national priorities would have to emerge incrementally from
“partisan mutual adjustment” among diverse power blocks.
Among stakeholders, corporate business interests were predominant because they were active and influential in virtually all policy areas, giving U.S. public policy in general a decidedly procapital cast relative to labor, consumers, the environment, and other interests (Bachrach & Baratz, 1962).
Congruently, policy making about national defense and military action had risen in importance and now influenced all other policy areas as well.
As President Eisenhower (1961)
warned in his
farewell address, military leaders and armament manufacturers had become a
“military-industrial complex” capable of influencing the entire direction of
American government.
Complexes differ from iron triangles in their command over resources that affect overall societal conditions, mass perceptions, and political priorities. Falling energy prices can help save a presidency, as they did in 2004. Military threats can rally support for the party in power, as happened after 9/11.
Fears of epidemics and biological weapons can
fuel militarism and restrictions on civil liberties, as they did after the
anthrax mailings in 2001.
The same moral hazards exist for the corporate
and industrial interests that compose the economic side of
political-economic complexes because the national political agenda is the
primary factor affecting the income, importance, and long-term prospects of
the corporations involved.
In recent years, the main threats from these forms of corruption have come from innovative schemes to circumvent existing controls. A good example is how the savings and loan industry was looted in the 1980s.
Corporate leaders who were engaged in far-flung conspiracies to commit fraud finagled changes in regulatory policies and enforcement that allowed their frauds to go undetected until their banks had been plundered (Black, 2005; Calavita, Pontell, & Tillman, 1999). This special-interest corruption in the finance and banking industry was repeated little more than a decade later when Enron used its tight connections with the Bush-Cheney administration to evade controls on energy pricing and asset accounting (Munson, 2005).
The collapse of Enron and other financial
conglomerates led policy makers to strengthen regulations for monitoring
corporate accounting and holding corporate officers responsible for their
companies’ actions.
Much of the waste and incompetence of military contractors in Iraq have been attributed to politicization of the contracting process. In many cases, companies were selected solely on the basis of their ties to the Republican Party (see Scahill, 2007).
Similarly, in the system of influence peddling
by members of Congress, including Representatives Cunningham, Ney, and
Delay, large government contracts and specific legislation were traded for
cash payments, campaign contributions, jobs for relatives, and access to
corporate planes. Although additional reforms are needed, the procedures for
government contracting, accounting, and earmarking were tightened after
voters gave Democrats a majority in both the House and Senate in 2006.
It may be difficult to detect fraud in corporate
accounting, cronyism in government contracting, and influence peddling in
legislative earmarking, but no one doubts that such crimes are possible and
that regulators, investigators, and legislators need to guard against them.
When suspicious incidents occur that alter the nation’s objectives, disrupt presidential elections, provoke military action, or otherwise affect the national agenda, Americans tend to accept the self-serving accounts of public officials, seldom considering the possibility that such incidents might have been initiated or facilitated by the officials themselves.
The role and function of the universally understood concept of “agent provocateur” is grossly neglected in the idiom of American political discourse.
This mass gullibility, which itself invites
SCADs, is unlikely to change until SCAD detection and prosecution are
improved.
This includes the offices of the president and the vice president, the diplomatic corps, the nation’s intelligence agencies (notably, the CIA, NSA, and FBI), top leaders in the military, private research organizations (such as the RAND Corporation), and certain military and intelligence contractors.
Significantly, intelligence contractors are
estimated to now account for 70% of America’s intelligence expenditures (Shorrock,
2008, pp. 19-20), leading some observers to speak of an
“intelligence-industrial complex” (Shorrock, 2008, pp. 12-13, 90, 162, 166,
168).
From the beginning, the apparatus had a presence internationally through the diplomatic corps and affiliations with the intelligence agencies of U.S. allies. But its international reach has been greatly expanded in recent decades because of America’s growing number of foreign military bases and its land- and space-based equipment for surveillance.
The United States has 725 foreign military
bases, and its forces are stationed in 153 foreign nations (C. Johnson,
2004, p. 154), in addition to an untold number of espionage bases.
Most of the nation’s offices for intelligence gathering and covert operations were removed from the armed services and placed under civilian control. The functions and purviews of different offices, even those within a single agency, were strictly delineated and separated in order that each office would have only a partial picture of the nation’s aims, tactics, weapons, and operations.
This administrative compartmentalization was intended to protect secrecy and to prevent policy interests, especially those of the armed services, from distorting intelligence.
However, compartmentalization also facilitates
the misuse of apparatus assets for purposes of domestic politics because it
leaves each component of an operation ignorant of the operation’s principals
and overall purpose.
The first covert operations of the apparatus were undertaken immediately after the end of World War II. In the late 1940s, the CIA made secret financial contributions to anticommunist political parties in Italy, France, and Japan. In Italy, it also bought Mafia help in keeping communists out of the dock workers’ union.
In the 1950s, it became actively involved in
coups against democratically elected regimes. After these coups, the
apparatus instructed and aided its coup partners in the use of state
terrorism for quelling unrest and opposition (see Blum, 2004; Klein, 2007).
Tape recordings of Richard Nixon in the White House reveal that the FBI colluded with Nixon to frame Alger Hiss (Summers, 2000, pp. 70-75).
Hiss was probably guilty of espionage, but the
FBI lacked proof, so Hoover tapped Nixon to interrogate Hiss in Senate
hearings. The FBI then forged documents to match Hiss’s typewriter, and the
documents were sufficient to convict Hiss of perjury. The FBI also fed
secret information to Joseph McCarthy, whose attacks on alleged communists
and communist sympathizers terrorized more-liberal public administrators,
intellectuals, artists, and others.
After the invasion failed, the apparatus began working with bosses in the American Mafia to engineer the assassination of Fidel Castro. In 1963, the apparatus directed a coup in Vietnam that resulted in the murder of President Diem, who had previously been installed with the help of the CIA.
From these initiatives, it would have been only a small step for the assassination capabilities of the apparatus to be directed at a domestic target.
In any event, as the apparatus was learning how to organize conspiracies to murder foreign leaders, the United States experienced an unprecedented rash of political assassinations and attempted assassinations.
The targets included,
In the late 1960s and early 1970s, the apparatus began to establish profit-making enterprises, which gave it financial resources beyond the knowledge and control of Congress.
Many of these enterprises were legitimate businesses. Perhaps the best example is Air America, which was the proprietary airline of the CIA. By the end of the Vietnam War, Air America had become the largest airline in the world.
The CIA also had front companies or “cutouts” in
many other industries related to its covert operations, especially public
relations, telecommunications, energy, and publishing.
The principals who secretly negotiated the arrangement in Paris reportedly included vice presidential candidate George H. W. Bush and former intelligence officers Bill Casey (Reagan’s campaign manager) and Robert Gates.
After the Reagan
administration took office, Casey became director of the CIA and Gates
became assistant director.
Given what is now known about Iran-Contra, it appears likely that the Iran-Contra operation grew out of the October Surprise agreement. At the direction of President Reagan and with the direct involvement of Vice President Bush, the apparatus began selling arms to Iran at highly inflated prices and funneling the profits to the Contras.
The Contras were also brought into the drug
trade and were given assistance in smuggling cocaine into the United States
(Ruppert, 2004; Webb, 1998).
The Watergate prosecutions, congressional investigations, and presidential tape recordings provide a thorough account of the break-ins and of the efforts by the president and others to cover-up Watergate’s connection to the administration. This official record has also been supplemented by the books of several investigative journalists and by the memoirs of Nixon’s chief of staff Bob Haldeman (1978) and Watergate burglars Howard Hunt (1974), Gordon Liddy (1980), and James McCord (1974).
Watergate suggests that SCADs are not so much
aberrations within the apparatus as they are predictable turns taken when
national security initiatives intersect with domestic presidential politics.
After all, he knew that the government had targeted him in the 1968 election. After he became president, FBI director Hoover informed him that, at the instructions of President Johnson, the FBI had placed wiretaps on the phones in Nixon’s airplane (Gray, 2008, pp. 161-162). President Johnson’s action in this regard implies that he, too, considered such espionage legitimate.
That Johnson and Nixon were from different
parties but were both able to use the FBI for political espionage indicates
that, by the late 1960s, apparatus capabilities were seen by the president,
the FBI director, and probably others at their level to be resources
appropriate for use in domestic politics.
After the FBI refused to wiretap reporters, Nixon and his team established the Special Investigative Unit in the White House to stop information from “leaking.”
This is why the White House staff referred to
Howard Hunt and Gordon Liddy as the “plumbers.” Wiretaps were placed on the
telephones of reporters as well as administration officials. Among the
latter was Henry Kissinger, who was discovered to be one of the media’s
sources.
Finally, as the 1972 election approached, Hunt and Liddy were brought into Nixon’s reelection campaign to handle the campaign’s security and intelligence activities.
Hunt and Liddy prepared an extensive plan for, among other things, infiltrating the primary and general election campaigns of the Democrats, disrupting the Democratic National Convention, and luring convention delegates into compromising liaisons with prostitutes. Also part of this plan was placing wiretaps on two telephones in the headquarters of the National Democratic Party and searching through the files in the office of the Democratic Party Chairman.
The plan was recognized at the time to be risky
and illegal, but it was approved by top officials in the White House and by
the Committee to Re-elect the President.
The plumbers had broken into Fielding’s office in search of information needed by CIA profilers for preparing an analysis of how to “break” Ellsberg emotionally.
The other burglaries in the D.C. area similarly targeted the offices of physicians and psychiatrists whose patients were Nixon’s opponents or their wives. This MO is consistent with one of various forms of psychological warfare practiced by the apparatus, which had conducted years of psychological research to learn how to psychoanalyze people from a distance, identify their psychological conflicts, and create pressures in their lives to produce emotional breakdowns (Marks, 1979).
Hunt and Liddy may have been just one compartment in a larger assemblage of operatives who were conducting psychological warfare against many of Nixon’s “enemies.”
This would explain why “Deep Throat” (deputy
director of the FBI Mark Felt) told Bob Woodward that almost the entire law
enforcement wing of the national government was involved in the Watergate
operation and cover-up and that bugs had been placed in the homes of
Woodward, Bernstein, and Washington Post editor Ben Bradlee.
Charles Colson, one of Nixon’s main political advisors in the White House, hinted as much in taped conversations with the president (Kutler, 1997, p. 194).
Furthermore, Liddy (1980, pp. 207-210) reports in his memoirs that in 1972 Colson instructed Hunt and him to prepare a plan for assassinating Jack Anderson, an investigative journalist. Although Anderson’s murder was called off, Hunt and Liddy were quite willing to perform the operation and viewed it as a reasonable assignment.
For that matter, shortly after the Watergate burglars were arrested, Liddy (1980, pp. 257-258) told John Dean that he would understand if he, Liddy, were slated to be killed; he asked only that the hit occur someplace other than at his home, where his wife and children might come to harm.
One death that a grand jury suspected had been
arranged by the White House was that of Dorothy Hunt, Howard Hunt’s wife,
who was killed in an airplane crash not long after she had begun
blackmailing Nixon to provide financial support for the Watergate burglars
during their incarceration (Kutler, 1997, p. 474).
The Watergate investigations exposed the crimes of high-ranking public officials, and a number of officials went to jail.
But few changes were made to the organization, procedures, or oversight of national security agencies even though they had been quite willing to go along with Nixon’s crimes. In the aftermath of Nixon’s resignation, the Church Committee hearings on the CIA uncovered many illegal and illegitimate activities by the apparatus, including assassinations of foreign leaders, coups, collaboration among state agents with criminal organizations, illegal domestic surveillance, and more.
They also turned up evidence of CIA and FBI
involvement in U.S. domestic politics, including not just Watergate and the
dirty tricks of Donald Segretti but also the secret provision of funds to a
wide range of civic organizations and the use of illegal wiretaps and agent
provocateurs against the civil rights and antiwar movements (C. Johnson,
2004; Wilford, 2008; Wise, 1976).
The suspicion was voiced by others; for example,
Bernstein and Woodward (1974) speculated in their book on Watergate that
Nixon might have been behind the attempted assassination of George Wallace.
But public officials were seemingly unwilling to take their suspicions this
far; the post-Watergate reforms targeted isolated abuses of power rather
than the general problem of elite political criminality in the national
security state.
Haig later played a role in Iran-Contra when he
approved weapons sales to Iran not long after Ronald Reagan’s inauguration (Kornbluh
& Byrne, 1993). George H. W. Bush had been a frequent visitor to the Nixon
White House after Nixon had picked him to be chairman of the Republican
National Party.
Although Bush was CIA director for only one
year, he became enormously popular in the apparatus because he kept the
CIA’s secrets and protected the CIA professionals from exposure and
prosecution in the aftermath of Watergate (Bowen, 1991, pp. 41-58).
In the 1980s, Cheney was a member of Congress. Serving on the House Intelligence Committee, he had been briefed on aspects of the Contra program, and he had been a vocal defender of the Iran-Contra project when it was first investigated by Congress (before an independent prosecutor was appointed).
Others directly involved or associated with Iran-Contra who returned to power with Bush- Cheney included,
Shortly before the 2003 invasion of Iraq, the president changed long-standing policy to allow the vice president to declassify state secrets (Rich, 2007).
A few months later, after Joseph Wilson challenged the administration’s claims about Iraq seeking to acquire uranium in Africa, the vice president informed his aid Scooter Libby of Plame’s status. Libby then leaked this information to the press and to others in the administration who also leaked it to the press.
These circumstances suggest that Libby was following the orders of the president and the vice president, but Libby alone was indicted, and only then for committing perjury when he denied having leaked Plame’s identity to reporters.
Without a confession from Libby
implicating
Cheney and Bush, no one was willing to take action against either the
president or the vice president, both of whom appear to have been part of a
criminal conspiracy to expose the identify of a covert agent in a time of
war.
In both cases, the presidents were misleading
the public about their foreign policy motives and initiatives, their
credibility was threatened by whistleblowers who took their stories to the
New York Times, they responded by using national security assets (operatives
for Nixon, and information for Bush) in an effort to undermine the
whistle-blowers’ credibility, and when the underlings who had carried out
their criminal schemes were apprehended and prosecuted, they put their
reelections ahead of all considerations of loyalty and culpability, denied
all knowledge and involvement in the crimes, and let their minions take the
full blame.
Just as the Watergate break-ins were simply the tip of Nixon’s criminal iceberg, Plamegate was only one small element in a much larger pattern of political lawlessness.
Much evidence indicates that, in addition to outing Valerie Plame, the Bush-Cheney administration manipulated and distorted intelligence to,
There is also circumstantial evidence that the Bush-Cheney administration may have somehow been involved in 9/11.
The administration ignored many warning signs that,
Evidence also indicates that the Pentagon was
hit by a missile rather than a passenger plane and that Flight 93 was
exploded at high altitude.2
Recently, many mainstream scholars and journalists have concluded that American democracy is becoming increasingly corporatist, imperialistic, and undemocratic (Bacevich, 2005; Dean, 2007; Goldsmith, 2007; Greenwald, 2007; C. Johnson, 2004; Klein, 2007; Mayer, 2008; Savage, 2007; Shorrock, 2008; Wolin, 2008).
However, mainstream authors have seldom
considered the possibility that authoritarian tendencies in American
politics are being systemically engineered by top-ranking civilian and
military officials. Rather than thinking in terms of high crimes, their
diagnoses have blamed abstract institutional weaknesses or isolated failures
of leadership.3
This sub-rosa manipulation of domestic politics is an extension of America’s duplicity in foreign affairs and draws on the nation’s well-developed skills in covert operations. Through its experience with covert actions, the National Security Apparatus has developed a wide range of skills and tactics for subverting and overthrowing regimes, manipulating international tensions, and disrupting ideological movements.
The United States, or more specifically
presidential administrations, uses these skills in combination with visible
foreign policies to maximize the impact of both the visible and invisible
sides of their efforts.
Although the implications of this policy for popular control of government are seldom examined, the policy itself was and is no secret.
As an assistant secretary of defense said in response to claims that public opinion had been manipulated during the Cuban missile crisis,
Richard Nixon put it more bluntly.
In claiming that the president has the power to break the law when protecting national security, he said,
U.S. capabilities for covert operations enter the nation’s domestic politics as SCADs in at least two ways.
Sometimes, the process is rather haphazard. In Watergate, for example, the Nixon administration was using covert-action skills domestically in legitimate matters of national security when it diverted these skills, first, to attack Daniel Ellsberg and perhaps other political enemies and, subsequently, to gain advantage in the 1972 presidential election.
Generalizing from this example, covert-action capabilities can end up being exploited for SCADs because the officials who control these capabilities are operating in an intensely political environment, and they occasionally succumb to temptations to use their national security powers for personal or partisan advantage.
The idea that SCADs are opportunistic gambits in
presidential politics was the conclusion reached in the official
investigations of both Watergate and Iran-Contra.
Furthermore, arranging these shootings and pinning them on patsies would have required many operatives, extensive resources, and a variety of skills.
Similarly, if the attacks of 9/11 were executed
or somehow facilitated by U.S. public officials - as much evidence suggests
- a number of agencies would have had to have been involved, including
elements of the Department of Defense, the CIA, and the FBI.
The potential for SCADs to be committed opportunistically in presidential politics can be reduced statutorily by mandating procedures for investigating election problems, defense failures, assassinations, and similar incidents.
As it stands, events with profound implications for the nation and the world are left to be investigated on an ad hoc basis; procedures for controlling crime scenes, inventorying evidence, interviewing suspects, interpreting evidence, overseeing the investigative process, and reporting findings are developed on the spot in the aftermath of the tragedies, when the nation is in shock and the perpetrators may be covering their trail.
Public officials or their agents lost, discarded, or destroyed,
Reducing American democracy’s vulnerability to manipulation by military and intelligence elites will require amendments to the U.S. Constitution to strengthen the role of Congress and the public in national security policy making.
In particular, revisions are needed to the constitutional procedures for declaring, fighting, and ending wars (Bacevich, 2005; Byrd, 2004; Dean, 2007; Fisher, 2004).
SCADs usually draw on the skills of covert action and are often connected to secret foreign-policy objectives, from discrediting dissidents and stopping leaks to fabricating intelligence and provoking wars. The United States has become extensively involved in covert operations overseas because the nation’s leadership is no longer adhering to the Constitution’s requirements governing military action.
The last military action for which Congress issued a declaration of war was World War II. Since then, the introduction of nuclear weapons has made Congress reluctant to authorize the kind of uninhibited aggression that a declaration of war might unleash.
However, the Constitution contains no process
for authorizing limited wars or for ensuring that Congress can end such wars
at its discretion. In large part this is why the role of Congress and the
president became so muddled during the Vietnam War. The failure of the War
Powers Act to correct this situation was demonstrated all too clearly after
2006 by legislative-executive conflict over the occupation of Iraq.
The potential for SCADs is large because elite political conspiracies are difficult to detect and investigations are in the hands of the very people who actually need to be scrutinized. However, social scientists have the requisite conceptual resources, methodological skills, and scholarly independence to make antidemocratic corruption visible.
Once it is rendered visible, it will no longer
be tolerated.
See, for example, Griffin (2004, 2005), Hufschmid (2002), Paul and Hoffman (2004), and Tarpley (2005). There is also a “9/11 Truth Movement,” which is producing a detailed studies of 9/11 issues and anomalies.
For example, see www.911truth.org, www.911scholars.org, and www.911essentials.com.
Leadership failures that have been blamed include opportunistic responses by political elites to terrorist threats, exaggerated fears of terrorist attacks, and politicization of intelligence gathering and interpretation to support ideological positions.
An important exception to this mainstream failure to think in terms of high crimes is (Neal S.) Wolin (2008), who argues that American democracy is becoming deeply corrupt. But even in Wolin’s account, America’s corruption is more moral than criminal.
He says that elites and masses alike have lost sight of democratic values because they have become preoccupied with material rewards and imperial ambitions.
Hence, Wolin calls for a renewed ethics of
democratic citizenship, not heightened vigilance against criminal
conspiracies in high office.
|