|

by Thomson/Reuters
14 May 2017
from
NewsMax Website

Signage is seen outside The Royal London Hospital
in
London on May 14, 2017.
The
unprecedented global cyberattack
has hit
more than 200,000 victims
in
scores of countries.
AFP
PHOTO / Niklas HALLE'N
The NSA
discovered how to secretly hack Windows, but didn't
tell anyone.
When the hack
was leaked, real hackers jumped on it and turned the
world upside-down.
This means the
the NSA is a ‘Black-Hat” hacker. White-Hat hackers
have a moral code of ethics to always disclose a
known vulnerability as soon as it is discovered.
Technocrats at
the NSA see no need for disclosure of any kind, and
will likely never be held accountable for the
billions in damages caused by the Wannacry
ransomeware virus.
Source
More
Disruptions Feared from Cyber Attack - Microsoft Slams Gov't Secrecy
Officials across the globe scrambled over the weekend to catch the
culprits behind a massive ransomware worm that disrupted operations
at car factories, hospitals, shops and schools, while Microsoft on
Sunday pinned blame on the U.S. government for not disclosing more
software vulnerabilities.
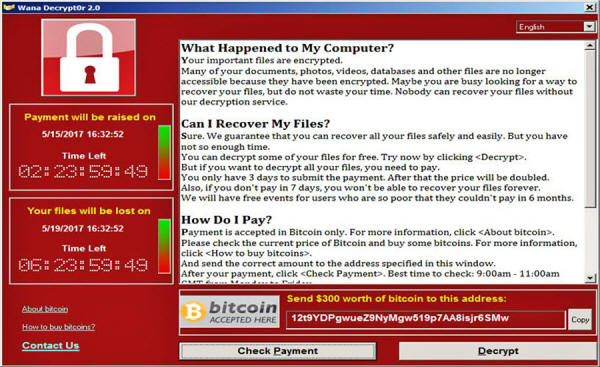
Cyber security experts said the spread of the worm dubbed
WannaCry - "ransomware" that locked
up more than 200,000 computers in more than 150 countries - had
slowed but that the respite might only be brief amid fears new
versions of the worm will strike.
In a blog post on Sunday,
Microsoft
President Brad Smith appeared to tacitly acknowledge what
researchers had already widely concluded:
The ransomware attack
leveraged a hacking tool, built by the U.S. National Security
Agency, that leaked online in April.
"This is an
emerging pattern in 2017," Smith wrote.
"We have seen
vulnerabilities stored by the CIA show up on WikiLeaks, and
now this vulnerability stolen from the NSA has affected
customers around the world."
He also poured fuel on a
long-running debate over how government intelligence services should
balance their desire to keep software flaws secret - in order to
conduct espionage and cyber warfare - against sharing those flaws
with technology companies to better secure the internet.
"This attack provides
yet another example of why the stockpiling of vulnerabilities by
governments is such a problem," Smith wrote.
He added that governments
around the world should,
"treat this attack as
a wake-up call" and "consider the damage to civilians that comes
from hoarding these vulnerabilities and the use of these
exploits."
The
NSA and White House did not immediately respond to
requests for comment about the Microsoft statement.
Economic experts offered differing views on how much the attack, and
associated computer outages, would cost businesses and governments.
The non-profit
U.S. Cyber Consequences Unit
research institute estimated that total losses would range in the
hundreds of millions of dollars, but not exceed $1 billion.
Most victims were quickly able to recover infected systems with
backups, said the group's chief economist, Scott Borg.
California-based cyber risk modeling firm
Cyence put the total economic
damage at $4 billion, citing costs associated with businesses
interruption.
U.S. President Donald Trump on Friday night ordered his
homeland security adviser, Tom Bossert, to convene an
"emergency meeting" to assess the threat posed by the global attack,
a senior administration official told Reuters.
Senior U.S. security officials held another meeting in the White
House Situation Room on Saturday, and the FBI and the NSA were
working to help mitigate damage and identify the perpetrators of the
massive cyber attack, said the official, who spoke on condition of
anonymity to discuss internal deliberations.
The investigations into the attack were in the early stages,
however, and attribution for cyber attacks is notoriously difficult.
The original attack lost momentum late on Friday after a security
researcher took control of a server connected to the outbreak, which
crippled a feature that caused the malware to rapidly spread across
infected networks.
Infected computers appear to largely be out-of-date devices that
organizations deemed not worth the price of upgrading or, in some
cases, machines involved in manufacturing or hospital functions that
proved too difficult to patch without possibly disrupting crucial
operations, security experts said.
Microsoft released patches last month and on Friday to fix a
vulnerability that allowed the worm to spread across networks, a
rare and powerful feature that caused infections to surge on Friday.
Code for exploiting that bug, which is known as "Eternal
Blue," was released on the internet last month by a
hacking group known as the Shadow Brokers.
The head of the European Union police agency said on Sunday the
cyber assault hit 200,000 victims in at least 150 countries and that
number would grow when people return to work on Monday.
|



