|

by Dennis Anon
February 24,
2018
from
Privacy Website

If you use a web browser like,
-
Chrome
-
Firefox
-
Internet Explorer
-
Edge
-
Safari,
...then you've probably
picked up a few cookies along the way.
Cookies are used to
remember things about websites:
your login
information, what you have in your shopping cart, what language
you prefer...
They are created by
websites and sit in your browser until they expire.
Some cookies are harmless, but others remain active even on websites
that they didn't originate from, gathering information
about your behavior and what you click on.
These are called
third-party persistent cookies or, more colloquially, tracking
cookies.
Tracking cookies can be so invasive that many antivirus programs
classify them as spyware. Despite their bad reputation, they have
become so ubiquitous that it's nearly impossible to avoid them.
In this article, we'll go
into detail and explain how tracking cookies record your web
activity, why they're so popular, and how to stop them.
Types of
cookies explained
First, let's briefly cover the main types of cookies:
-
session cookies
-
persistent
cookies
Whenever you go into your
browser settings and clear your cookies, you're deleting the
persistent cookies.
Session cookies
The most basic type of cookie is a session cookie. Session
cookies only exist in temporary memory and are deleted when you
close the browser.
Any cookie created
without an expiration date is automatically a session cookie.
A common uses for
session cookies include remembering what's in your shopping cart
on an ecommerce site (although most modern ecommerce sites now
store this info in a database on their servers).
First-party persistent cookies
Persistent cookies are written onto your device's memory and
come with an expiration date.
They are only used by
the website that created them, and can last however long the
website dictates. They remain on your device even after you
close your web browser.
Your web browser uses
first-party persistent cookies for many quality-of-life
enhancements, like remembering that you're signed in so you
don't need to log in every time you visit the same site.
Third-party persistent cookies
Third-party persistent cookies, also known as tracking cookies,
are the main focus of this article.
Like their
first-party brethren, these cookies are stored in your device's
memory and have a set expiration date. Unlike the first-party
variety, however, third-party persistent cookies are accessed on
websites that didn't create them.
This allows the
cookie's creator to collect and receive data any time the user
visits a page with a resource belonging to them.
Where do
tracking cookies come from?
Websites today are rarely made up solely of code and content created
by the website owner or administrator.
Instead, they use
resources from other sites to build and add functionality to their
web pages. These resources are often useful and even essential for a
website to compete. Unfortunately, those same resources are often
the biggest perpetrators of online tracking.
Some of the most common
resources that use tracking cookies include:
You don't even need to
click on an ad or social media sharing button for a tracking
cookie's information about you to be transmitted back to a server
owned by the person or company who created it.
As soon as you load the
page, the cookie is sent to the server where it originated. If no
cookie exists yet, the resource can create one.
Let's say I write a blog post an include an image that's hosted on
another website. The other website can create a cookie or send and
existing one to its server, even though I'm not actually on that
website; I'm just loading a resource from it.
Similarly, most ads and
widgets aren't hosted by the websites they reside on. They are just
resources pulled from third-parties, and they all use cookies.
According to
The Guardian, some of the
biggest companies using tracking cookies include:
-
AddThis
-
Adnxs
-
Doubleclick
-
Facebook
-
Google
-
Quantserve
-
Scorecard
Research
-
Twitter
-
Yieldmanager
What do
tracking cookies know about me?
Tracking cookies are usually used for advertising purposes,
retargeting in particular.
Retargeting is a tactic
that often relies on tracking cookies to show ads to people who have
previously visited a specific site or shown interest in a particular
product.
If you've ever bought or
even looked at a product on Amazon and then started seeing ads for
similar products on other websites, you've been retargeted.
Here's a simplified step-by-step explanation of how retargeting
works:
-
You pick up a
tracking cookie on your favorite blog or shopping site. That
cookie contains a unique ID that doesn't identify you
personally, but does identify your web browser.
-
The owner of the
shopping site signs up and pays for an advertising platform
like Google.
-
Google's ads
aren't static; when you visit other websites that use Google
ads to make money, the website sees the cookie and sends it
to Google through the ad. Google sees the unique ID stored
in the cookie and recognizes that it came from your favorite
shopping site.
-
Google then shows
an ad for the shopping site accordingly.
Likewise, other
advertisers on Google's ad network can use that cookie, too, if your
advertising profile meets their criteria of the target audience.
It doesn't only benefit
the site where you picked up the cookie.
This might seem harmless at first, but those tracking cookies can
start racking up a lot of information about how you browse the web.
Google's ads are everywhere, and while it's the largest online
advertising company in the world, there are many, many others.
Because of this,
advertising companies can cobble together a history of what websites
you visit, in what sequence, and for how long. When cookies are sent
back to their servers, they often include information about the
previous site that a user visited, called a referrer URL.
Browsing history is just the start.
Tracking cookies can record all
kinds of information:
search queries, purchases, device information,
location, when and where you saw previous advertisements, how many
times you've seen an ad, and what links you click on.
All of this and more is collected, often without your consent or
knowledge. In the UK and EU, websites are required to notify users
if they use tracking cookies.
In the US and other countries,
however, all of this data is hoarded in the background.
What makes a
cookie?
If you examine the actual contents of a cookie file, none of this is
obvious. Cookies only consist of three components: name, value, and
attributes.
Using the Chrome
extension EditThisCookie, we can see what makes up a cookie:
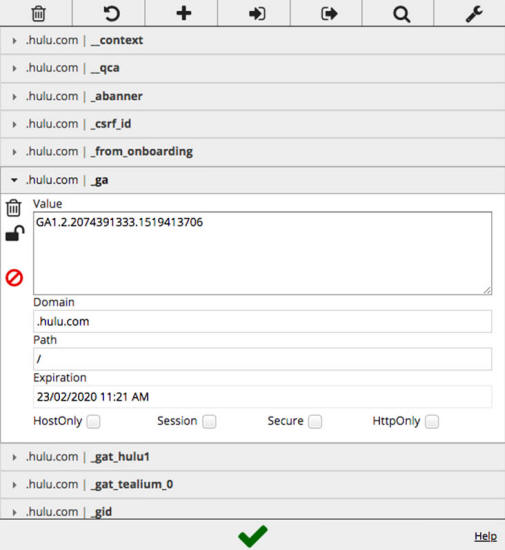
Google Analytics cookie
from
Hulu.com
Name is used by websites and advertisers to identify cookies and
what they're used for.
The value component is where your unique advertising ID stored so
that the tracker's creator can identify you when you visit other
websites. It usually appears as a seemingly random string of numbers
and digits, but in some cases it's not random and can contain coded
information as laid out above.
Attributes include characteristics of the cookie like:
-
When the cookie
expires. If no expiration date is set, the cookie ends when
the browser is closed. Tracking cookies always have
expiration dates.
-
If the cookie can
be used by other domains.
-
Whether the
cookie can be sent over an insecure connection or not.
Essentially, it checks for HTTPS.
-
Whether the
cookie can be accessed through JavaScript. Disabling this
prevents cross-site scripting (XSS) attacks that can be used
to steal login credentials and modify cookies for nefarious
purposes.
How to stop
tracking cookies
The first step toward preventing tracking cookies from monitoring
your behavior is to delete the ones you already have.
You can clear you cookies
in your browser settings. If you're not sure how, check out
this guide on clearing cookies for
all the major browsers and operating systems.
Your browser doesn't distinguish between persistent cookies that
perform useful tasks like keeping you logged into a website from
those that invade your privacy and track you around the web.
When you clear cookies in
your browser, all of them are deleted.
Do not track
Somewhere in your browser settings you'll find an option to
toggle on Do Not Track.
Enabling this feature
will send a request for the website you're currently on to
disable its cross-site user tracking of individual users. This
includes tracking cookies.
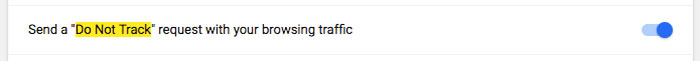
While some sites honor your choice to opt out with Do Not Track,
many will not.
Do Not Track does not
add any technical limitations and there's no enforcement from
any authority. That means there's no consequences for websites
that ignore your opt-out request and use tracking cookies
anyway.
You should definitely enable Do Not Track in your browser, but
you'll need to go a step further if you want to put a halt to
tracking cookies.
Keeping track of where all the cookies in your browser come from
and whether they track you would be a very tedious task.
Instead, you can install an anti-tracking browser extension to
stymie tracking cookies for you.
Privacy Badger and Disconnect are two good options. An ad
blocker like Adblock Plus can help, too.
All of these not only
make the web more private, they also speed up page load times by
blocking third-party elements.
Privacy Badger
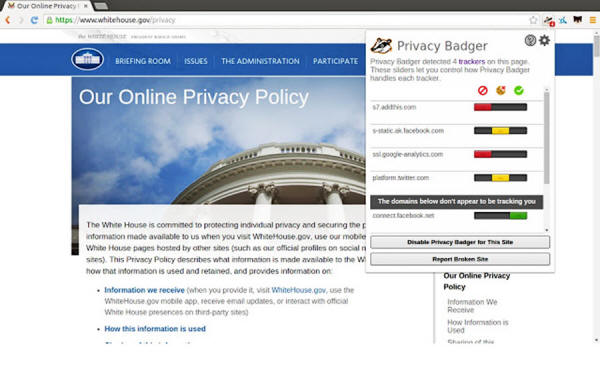
Created, by the Electronic Frontier Foundation,
Privacy Badger is a plugin for
Firefox and Chrome that automatically blocks advertisers that
use tracking cookies from loading any more content in your
browser.
It does this by
keeping track of third-party domains that embed images, scripts,
and advertising into pages that you visit. The extension doesn't
use a blacklist of known tracking sites.
Instead, it observes
the behavior of third-party domains on web pages and blocks them
if they collect unique identifiers.
Privacy Badger also protects against canvas fingerprinting and
super cookies, which we'll explain a bit later.
Disconnect
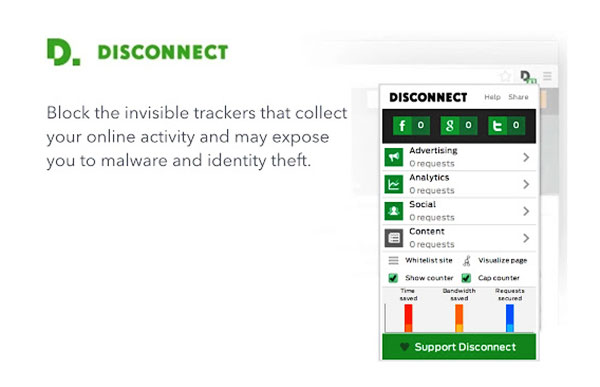
Disconnect automatically
detects when your browser connects to anything other than the
site you are visiting.
It then categorizes
those requests and blocks them, save for requests that are
necessary for the actual content of the site. The user can
choose to allow through other categories like analytics,
advertising, and social on an as-needed basis, or even allow
trackers through individually.
Disconnect makes several useful tools for improving privacy and
performance, but for the purposes of this article we're mainly
concerned with the free private browsing add-on.
Adblock Plus
Adblock Plus, not to be
confused with AdBlock, is the most popular ad blocking browser
extension on the web.
Advertisements are
the biggest perpetrators of online tracking, so this plugin can
be very effective. Unlike Disconnect and Privacy Badger, Adblock
Plus utilizes a blacklist of known domains that serve
third-party ads and blocks them accordingly.
Ads are just one part of the equation, so I recommend pairing
ABP with one of the other extensions.
Alternatively, you
can add additional blacklists created by the community to block
other third-party website elements that use tracking cookies,
such as social media widgets.
Other tracking
methods
Tracking cookies are not a new technology.
They've been in use for
over a decade and little has changed as far as the way they work.
Despite that, they provide a simple, accurate way to track and
record user behavior across the web, and they aren't going away
anytime soon.
That's not to say tracking cookies are the only way third parties
monitor what you do online.
Data mongers have several
tools at their disposal to stay locked onto you.
IP address
Even before there were cookies, there were
IP addresses. Every
device connected to the internet is assigned a unique IP address
that allows your device to communicate with other devices.
IP addresses are a
core component of how the internet works. But because they are
unique, they can be used to track you...
Your public IP address is made up of a string of numbers and
decimals. It changes periodically and is associated with your
location. If you connect to a different Wi-Fi network, for
example, you are assigned a new IP address and your old one is
recycled and assigned to someone else.
So it's not the most
enduring or accurate way to target someone, but it's easy and it
works.
To avoid being tracked by your IP address, I recommend using
a VPN. A VPN encrypts all of
the internet traffic on your device and routes it through an
intermediary server in a location of your choosing.
This masks your real
IP address with that of the VPN server, and that IP address is
usually shared with dozens, if not hundreds of other users,
making it nearly impossible to trace activity back to one
individual.
Referrer URLs
A referrer URL is the web address of the previous website where
you clicked a link to get to the current website.
For example, if you
found Privacy.net through a Google search and clicked on a link
to this article in the search results, the referrer URL for this
page would belong to Google.
Referrer URLs can be
used for several reasons, and recording your browsing history is
one of them. When cookies are sent to the server that created
them, they often contain referrer URLs.
But referrer URLs
don't require a cookie and the same information can be requested
from a website via other means.
Web beacons
Pixel tags, also called pixel tags, are little segments of code
on web pages that check whether you have accessed some content.
Web beacon is
actually an umbrella term for several similar techniques.
Web beacons can be hidden inside content elements of a web page,
making them more difficult to prevent. They can be hidden inside
images and other page elements to log user behavior and transmit
that data back to the website owner.
Web beacons are commonly used to check whether someone who
received an email actually read it. By embedding a pixel tag in
an email, the email must load a resource from a third-party.
When this happens,
the resource can request the recipient's IP address, timestamp,
type of browser, and whether the resource owner already set a
cookie in this browser.
Like cookies, the
server can store all of this information and associate it with
the user's unique tracking ID.
Browser fingerprinting
Browser fingerprinting is an emerging technique that's getting
more and more accessible and is notoriously difficult to shake.
A website can glean a
lot of information about your web browser through server-side
access logs and client-side Javascript and Adobe Flash.
This information
includes but is not limited to:
-
Browser model
and version (user agent string)
-
Language
-
Time zone
-
List of
plugins/extensions
-
Fonts and
font size
-
Screen
resolution
-
Do Not Track
status
-
Several other
browser settings
-
Whether
cookies are allowed
-
Protocol
-
URL requested
-
IP address
-
Referrer URL
Even if you connect
to a VPN to hide your IP address and block tracking cookies, all
of the other information can form a combination so specific that
the resulting profile can only plausibly belong to a single
person or small group of people.
Attempting to alter
your browser settings and install more plugins only makes you
stand out more.
You can disable Javascript using a plugin like NoScript or
ScriptSafe to prevent the collection of most of this data, but
many websites rely on Javascript to function, so chances are
you'll be forced to enable it at some point.
The only other
alternative is to use two browsers:
Cookie syncing
Most tracking cookies can only be used by the domain that
created them.
Advertising companies
are responsible for many domains that serve tracking cookies,
each with its own database of user profiles and audience
segments used to target you with ads.
Save for Google, most of these ad companies aren't prolific
enough to be everywhere on the web at once, which leads to gaps
in their data. Enter cookie syncing, the practice of combining
advertising data sets to create more accurate and comprehensive
tracking profiles.
Cookie syncing occurs when two advertising companies partner up
or acquire one another.
This consolidation
helps them compete with Google, but also has an adverse effect
on users' privacy.
Supercookies
Most cookies are tied to specific domains, such as "google.com".
Supercookies are
associated with top level domains like ".com" and ".org". This
allows them to affect requests for cookies from websites that
use those top level domains.
For example, a
supercookie that uses the ".net" top-level domain could disrupt
or impersonate requests from Privacy.net.
Not only could supercookies be used to track you across the web,
they can also be used for malicious purposes like changing user
information or forging a login.
For these reasons,
most modern browsers block supercookies.
They're worth
mentioning but probably aren't much of a threat to you.
|







