|

by Amakiri Welekwe
September 2018
from
VPNMentor Website

What is the
Dark Web?
You already know about websites like Wikipedia, Google, Amazon,
YouTube, and Facebook.
But they're only a small
part of the internet. Beyond those popular websites are sites hidden
away and not readily available to the general public. That space is
where
the Dark Web and the Deep Web exist.
The
Dark Web, or Darknet, is a general
term for a collection of websites on an encrypted network with
hidden IP addresses - all of which gives users strong anonymity
protection.
Because they are not
indexed by traditional search engines, you can only access them with
special anonymity browsers, such as,
You can read more about how Tor works
here.
The Dark Web
is Not the Same as the Deep Web
The Deep Web is all the sites on the web that can't be reached with
a search engine.
Although this includes
sites on the Dark Web, it also includes sites that serve more
mundane functions, such as,
These are found and accessed directly with a URL or IP address, and
are hidden behind firewalls, paywalls and HTML forms.
Because all these other
pages are included in the Deep Web, the Deep Web is actually far
more vast than the regular internet (also known as the Clear Web).
How to Access
the Dark Web Safely
The main gateway to the Dark Web is the Tor browser.
This is an
encrypted network of volunteer relays around the world through which
users' internet connections are routed.
Although the relays are an integral part of what makes Tor
anonymous, they can also lead to slow connections. This is because
rather than connecting directly to the server of the website you
want to get to, you first have to go through the relays, which are
often purposely scattered around the globe.
Also, since the system is
decentralized, not all the relays have the same CPU, meaning that
while some are fast and powerful, others might operate at a snail's
pace.
The easiest way to browse web pages is to download and install the
Tor browser bundle.
Tor URLs end in the
suffix .onion. Unlike .com websites, the URLs are usually complex
and difficult to remember, and websites will often change their URLs
in order to evade detection and
DDoS attacks.
When you're on the Dark Web, ISPs - and by extension, the government
- might not be able to view your activity, but they will know you
are on the Tor Network.
This alone is enough to raise eyebrows in
some countries.
That's why we recommend accessing Tor using a VPN. That way, your
internet traffic is routed through the VPN before going through the
Tor Network and finally reaching its destination. With this method,
your ISP only sees the encrypted VPN traffic, and won't know you're
on the Tor network.
The major concern with using Tor over a VPN is that it requires you
to trust your VPN provider, as the provider may see that you are
using Tor.
To mitigate this issue,
use a VPN that does not log your activities, and connect to your VPN
before opening the Tor browser.
Use These
Steps as a Guide
Step 1 - Get
yourself a good VPN service
That means one that doesn't keep logs, has no DNS leaks, is
fast, is compatible with Tor, and which (preferably) accepts
Bitcoin as payment. Here are some of the most trustworthy.
If
you're new
to VPNs, this
handy tutorial will teach you
everything you need to know.
For this example, we're using the VPN CyberGhost.
Open the VPN
and connect to a server in your chosen location. This will
change your IP address, making it appear as if you're connecting
to the web from a different location than your real one.

Step 2 -
Download and install the Tor browser bundle
Before you do though, check that your VPN is running. Also be
sure to download Tor from the official Tor project website.
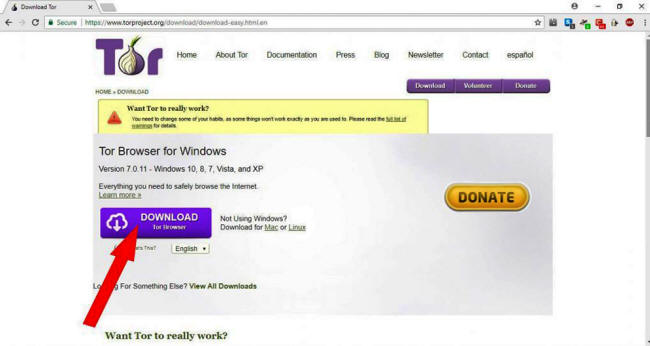
Once it's installed, look for the Tor Browser folder and click
on the "Start Tor Browser" file inside it.

A new window will open asking you to either click on the
"Connect" or "Configure" button. Click on the "Connect" option
to open the browser window.

Step 3 - Start browsing .onion websites
When you open Tor on your computer, you'll automatically be
directed to the search engine DuckDuckGo.
While
DuckDuckGo is
designed to provide extra privacy and encryption while searching
the web, you shouldn't think of it as the dark web version of
Google.
That's because even in Tor, DuckDuckGo searches the clear web.
That means if you do a keyword search, you're results are going
to be basically the same as what you would find on the regular
internet.
Fortunately, there are Dark Web search engines that will bring you
to .onion sites.
These include:
Just make sure to always
turn on your VPN before opening Tor and starting a web surfing
session.
The Dark Web Isn't
Just for Criminals
The anonymity provided by the Dark Web is certainly attractive to
those looking to buy or sell illegal goods such as drugs, weapons,
or stolen data.
But there are also legitimate reasons for using the Dark Web.
In past years it has
gained popularity as a safe haven for,
-
whistleblowers
-
activists
-
journalists,
...and others who need to share sensitive information, but
can't do so out in the open for fear of political persecution or
retribution by their government or other powerful actors.
Police and intelligence agencies also use it to monitor terror
groups and keep tabs on cybercriminals. Additionally, corporate IT
departments frequently crawl the Dark Web in search of stolen data
and compromised accounts, and individuals may use it to look for
signs of identity theft.
In many circles, the Dark Web has become synonymous with internet
freedom, especially as nation states continue to clamp down on it.
It now plays host to a
number of media organizations involved in investigative journalism,
such as
ProPublica and
The Intercept. Most notably,
WikiLeaks - the
website that publishes classified official materials - also has a
home on the Dark Web.
Even Facebook maintains a
presence there in order to make itself accessible in countries where
it is censored by the government.
5 Positive
Things to Do on the Dark Web
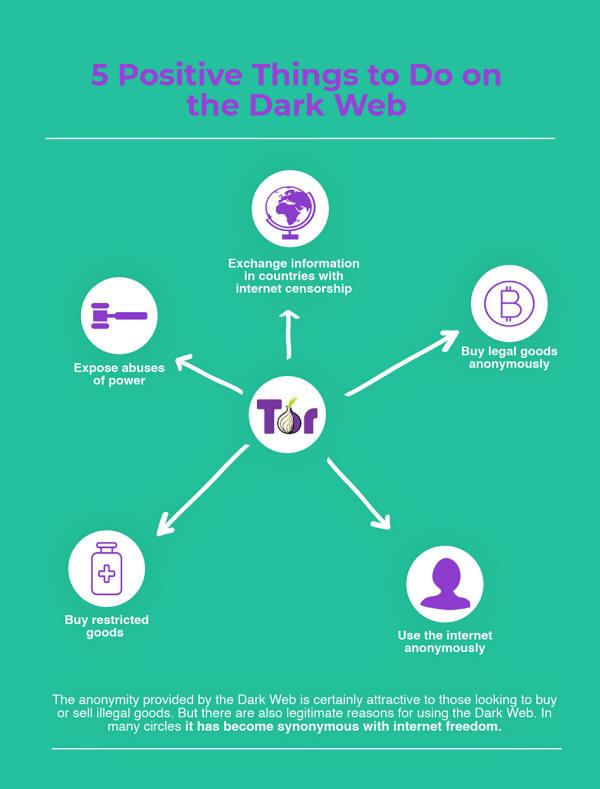
1. Exchange
information in countries with internet censorship
Tons of countries, like,
-
China
-
Qatar
-
Cuba
-
Turkey
-
Russia,
...censor online
content that promotes political dissidence or what they consider
obscene (e.g. content relating to homosexuality).
The Dark Web offers a
forum where none of these restrictions exist.
2. Expose
abuses of power
The Dark Web allows journalists and political activists to
report on stories that could get them in trouble with
dictatorial regimes or governments bent on infringing on an
individual's right to privacy.
As mentioned above, one popular way to share information
WikiLeaks.
If you have documents
you'd like to upload, you can do so here:
3. Buy restricted
goods
Although we at vpnMentor don't condone buying illegal goods, we
can't help but acknowledge certain instances in which such
purchases could be justifiable.
For instance, some painkillers and sleep aids that are common in
Europe are illegal in many Middle Eastern and Asian countries.
Plus, with an estimated 15.5% of Americans without health
insurance (and many more with high deductible plans) many people
have no access to the prescription medications they need.
That said, the lack of oversight on the Dark Web makes this
extremely risky - though some in dire straits are likely to take
that risk.
4. Buy
legal goods anonymously
Life is a rich tapestry, and we don't have to list the type of
stuff people buy that they might want to keep private.
Buying on
Dark Web marketplaces can add a level of privacy to your
shopping experience that you just won't find on Amazon.
And for the particularly security conscious, the Dark Web can
simply provide an extra layer of protection when buying
anti-surveillance tools.
It should be noted, however, that while the products themselves
may be legal, there are definitely instances in which sellers
hawk merchandise that's been illegally obtained or stolen.
5. Simply
use the internet anonymously
You might be surprised to find out the Dark Web hosts a lot of
websites similar to those you would find on the clear web.
These include,
Some popular email
services are,
Surfing the
Dark Web Isn't Illegal, but It Can be Dangerous
You can't be charged with a criminal offense for simply searching
the Dark Web, but you can get in trouble for using it to carry out
illegal activity.
Headlines about police operations that involved
the Dark Web and child pornography, drugs, or hackers dumping stolen
data are not infrequent.
Moreover, the anonymity of the Dark Web also makes it notoriously
risky.
Since there's no
oversight, it's teeming with scammers.
That said, one can
maintain one's safety by simply following the same basic security
rules that apply to the normal web:
Always be careful
about the links you click because some can be misleading, and
avoid sites or links that advertise illegal, disturbing, or
dangerous content you don't want to see.
Is the Tor
Browser Completely Anonymous?
In 2014 the FBI - with assistance from researchers at Carnegie
Mellon University - developed an exploit based on a Firefox
JavaScript flaw that successfully de-anonymized some Tor users,
including the operators of the popular
Silk Road website.
Although the
vulnerability that allowed those attacks was fixed within days of
its discovery, the incident nonetheless created fear among Tor users
that it may not be 100% secure after all.
Similarly, in October 2017 the security firm
We Are Segment
identified a vulnerability in Tor that was affecting some Mac and
Linux users.
This vulnerability, which
became known as
TorMoil, caused IP addresses to be leaked when users
accessed URLs that began with file:
//, rather than http:// or
https://.
We Are Segment notified
the Tor developers, who promptly fixed the error by updating to a
new version of the web browser.
In order to address these issues, the Tor Project has recently
improved security and privacy by strengthening its encryption.
It also gives web
developers the tools to build fully anonymous Darknet sites (known
as hidden services, or rendezvous points) that can only be
discovered by those who know the site's URL.
Extra
Precautions You Should Take to Maintain Your Anonymity
Although Tor is encrypted, and by using it with a VPN the IP
addresses of yourself and the websites you visit will be hidden, if
you want to remain totally anonymous on the Dark Web, you should
take the following extra security measures:
-
Never use your
real name or photos
-
Never use an
email address or even a password that you have used before
-
Instead, use an
anonymous encrypted email account and aliases that you have
never used before and that cannot be traced to you
-
Use an anonymous
Bitcoin wallet to make purchases. If you're new to Bitcoin,
or just want to learn more about it, you can find everything
you need to know here.
-
Disable
Javascript and don't install browser plugins, as they can be
manipulated into revealing your IP address
-
Do not change the
Tor browser window size to avoid browser fingerprinting
-
Don't torrent
over Tor, because even though your non-Tor IP address will
be anonymized to the tracker, it could still be visible to
the other peers in the network
-
Use HTTPS
versions of websites. This is because once your web traffic
goes through Tor's encrypted network, it still has to go
through an exit relay in order to reach the website you're
trying to get to. At this point your data could be exposed
to a third party, which could even insert an exploit into
your browser. URLs beginning with HTTPS prevent this.
-
Disconnect from
the internet before opening documents downloaded through
Tor, as downloading them while online could be used to
reveal your non-Tor IP address
-
Consider using
the
TAILS operating system (which is booted as a live DVD or
live USB), as this leaves no digital footprint on the host
machine
Criminal Cases
Involving the Dark Web
Although we believe the Dark Web should be used for promoting free
speech and bypassing censorship, there's no denying that the press
tends to focus on the more shady activity that goes on there.
Here are some of the most
high profile stories that have come out in recent years:
Silk Road:
Perhaps more than any
other website, the Dark Web brings to mind Silk Road.
Silk Road began as
the invention of a libertarian idealist who wanted to sell
home-grown mushrooms for Bitcoin, and ended up hosting 1.2
billion dollars worth of deals involving drugs, firearms, hits,
counterfeit cash, and hacker tools.
Five of the hits were
commissioned by the site's creator, Ross Ulbricht, known on Silk
Road as the Dread Pirate Roberts. Ulricht was ultimately caught
because of an old post to a regular website in which he promoted
Silk Road in its early days.
His mistake: using
his real email address.
AlphaBay:
Following the
shuttering of Silk Road,
AlphaBay became the most prominent Dark
Web marketplace.
When AlphaBay went
down in 2017, it was because of security missteps even more
basic than those of the Dread Pirate Roberts.
Among other
blunders, founder Alexandre Cazes used his legitimate email
address for communications on the site (pimp_alex_91@hotmail.com),
kept several unencrypted cryptocurrency wallets constantly open,
and re-used the same pseudonym on and off the Dark Web.
And when the cops
busted into his home in Thailand to arrest him, he was logged
onto the AlphaBay server with the username "admin."
The computer was
unlocked and unencrypted, and contained text files of passwords
used on the site, as well as a document listing the type and
location of all his financial holdings that was titled in bold
"TOTAL NET WORTH."
Several days after
his arrest, Alex Cazes was found dead in his prison cell,
apparently having committed suicide.
The Playpen
Case:
Although it only
existed for seven months, the child pornography site Playpen
managed to amass 215,000 users before the FBI gained access to
its host server via information provided by a foreign law
enforcement agency (which has not been publicly identified).
Instead of just
shutting the site down, the FBI continued to host it on its own
servers for two weeks, during which it used a Flash app to
capture 1,300 IP addresses belonging to site visitors.
This led to the
arrest of nearly 900 users around the globe, including Playpen's
creator, Steven Chase (may he burn in hell).
The Ashley
Madison Case:
In 2015, the hacker
group, the
Impact Team, breached a dating site for extramarital
affairs called Ashley Madison.
The hackers
threatened to release users' personal information unless the
website and its sister site, Established Men, were shut down. A
month later, when their deadline wasn't met, the Impact Team
started publishing data on the Dark Web.
Over the course of several dumps, information was revealed that
included the email and IP addresses of 32 million members, the email
correspondences of the CEO of Ashley Madison's parent company, and
the website's source code.
The hacker's stated
motivation was,
-
an objection to
the site's primary purpose
-
the site's
practice of forcing users to pay to delete their accounts
(which were even then not fully scrubbed from the servers)
Because Ashley Madison
didn't require email verification to create a profile, it would have
been easy to create accounts using someone else's email address, and
then use this to extort them.
Although we still don't
know who was responsible for the attack, one can speculate that they
were someone affected by these poor security practices.
On a final note,
VPNMentor
encourages everyone who uses the Dark Web
to do so responsibly. Offensive material can sometimes be just a
click away.
Browse at your own risk,
and never break the law...
|








