|

November
2017
from
DarkWebNews Website
Spanish
versiom
|
This
article and content are for general information purposes
only and are not intended to solicit illegal activity or
constitute legal advice.
Using drugs is harmful to your health and can cause
serious problems including death and imprisonment, and
any treatment should not be undertaken without medical
supervision. |

The Weird and Wonderful
Deep Web
As is implicit in its very name, the Deep Web can best be described
as a labyrinth of sorts, complete with infinitely fascinating
content.
There are millions of pages of interesting indexes, databases,
ideas, internal networks, communities and resources on the Deep Web,
both innocent and nefarious in nature.
Your TOR usage is being watched
In being introduced to the concept of the Deep Web, one fact always
manages to baffle the masses:
96 percent of the internet is not
indexed by search engines such as Google and Bing.
That means only a tiny portion of the World Wide Web is accessible
to you through standard means.
The average internet user is only
utilizing a portion of the potential the internet has to offer.
What is the
Deep Web then?
The Deep Web is all of the internet that cannot be found by regular
search engines, as the pages are not indexed in any way.

Search engines like
Google
have software called web crawler or web spiders.
They crawl
to find webpages.
That info is stored in
the search engine's index.
Google's
indexing system begins with a process called
"crawling."
Imagine a virtual
robot spider that starts at the home page and then crawls to and
from all the pages on the site that can be accessed by clicking all
the links.
Google then scans
the data and renders the content to send to Google's index servers.
From there, Google organizes the data by context and enters it into
a base of algorithms that make up the search engine.
Beyond the
boundaries of Google-able content is every bit of information you
can think of.

Google's index
has
information about
hundreds of billions of webpages.
It's size is
over 100,000,000 gigabytes.
Source
It contains a wide
range of information and data, from the inner-dashboard of your bank
account after you log in to private, password-protected websites to
unlisted articles and videos that might be censored or blocked in
certain countries.
Below the "surface
web," there are treasure troves of possibilities.
You just have to
know how to find them.
The Dark Web vs.
The Deep Web

Confusion
about
Deep Web and dark web is rampant.
Even big publications get it
wrong.
Contrary to popular
belief, the Deep Web and the dark web are actually two separate
definitions.
The media and,
frankly, much of the public that's unacquainted with the dark web,
tend to use these two concepts interchangeably. People often take
one to be the synonym for the other and vice versa.
This is a common
mistake for those who aren't familiar with the subject. But, the
difference between the dark web and the Deep Web is quite stark. The
two are made up of, and defined by, conflicting constructs.
As such,
the difference is worth clarifying.
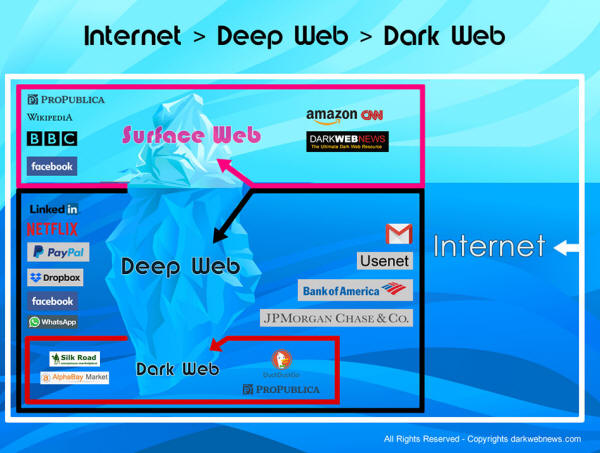
Info graphic
clarifies the concept of
internet, surface web,
Deep Web and dark
web
with examples and the metaphor of an ice berg.
The contrast
between the Deep Web and the dark web is often visually described by
comparing it to an iceberg. Imagine, for yourself, an iceberg.
Surface Web
Above water is all
content average internet users peruse on a daily basis.
This is your,
-
Facebook.com
-
reddit.com
-
justice.gov
-
harvard.edu
Deep Web
Right below the
surface of where the iceberg meets underwater is the Deep Web.
It's comprised of
the same general hostnames as sites on the surface web, but along
with the extension of those domains.
This is the
specific URL of your Facebook Messenger thread with a friend, or the
Department of Justice's public archival material, or Harvard's
internal communications system.
The Deep Web is the majority of the
internet as a whole.
Dark Web
The dwindling
portion at the very bottom of the iceberg is a subset of the Deep
Web that's only accessible through software that guards anonymity.
Because of this,
the dark web is home to entities that don't want to be found.
To expand on that
visual, it's necessary to explain that the
dark
web contains URLs that end in .onion rather than .com, .gov or .edu.
The network that
these .onion URLs reside on cannot be accessed with the same browser
you use to access your Facebook messages, the justice department's
archive or your Harvard email account. You can use a simple Chrome
or Safari to access these.
The dark web
requires a specific software program (the
Tor browser) to do the
trick, and it offers you a special layer of anonymity that the
surface web and the Deep Web cannot.
As such, the dark
web is a place for people and activities who don't want to be found
through standard means.
It's complete with
illegal trade markets and forums, hacking communities, private
communications between journalists and whistleblowers, and more.
How to Access the
Deep Web

Accessing the Deep
Web is not done through direct means since the information stored
within it exists in databases, making it impossible for conventional
search engines to obtain the data by just searching for it.
Search engines like
Google only organize and index data which is available on the
surface of the internet since in most cases, the URL is fixed,
subject to get picked up by Google's crawler bot, or there are no
special permissions required to view the web pages.
When crawling and
indexing pages, Google's bot system prefers URLs that follow
a simple directory structure; that is, a site's main content
should not be more than two subdirectory levels below the main
domain of the site.
One way to
visualize this concept is comparing it to a file-storing folder
hierarchy - you don't want to organize your desktop files in a way
that would be too complicated with multiple routes and directions;
that will completely defeat the purpose. The same idea applies here.
In the case where
passwords are needed, standard browsers cannot bypass this stage
since the information contained is highly confidential and so is the
need to protect it.
Due to
the sheer size of the Deep Web and the depth of the information
it contains, there's no real clear-cut way to access it.
There are different
methods by which you access your email address, social media
accounts or online portals, depending on the links you click in the
process, the redirects you encounter, the content you enter, etc.
The information
stored on the Deep Web is immense. And it's mostly publicly
accessible.
As mentioned
earlier, below the Deep Web is the dark web which can only be
accessed by the Tor browser.
A strict set of
guidelines ought to be followed to ensure your activities on the
dark web remain anonymous since Tor usage is often subject to
monitoring by authorities and also occasionally has vulnerabilities
that can leak your real IP address.
For more
information about how to properly get into and use the dark web,
check out a comprehensive guide on our
Access Dark Web page.
What Can be Found
on the Hidden Web?
The data found on
the Deep Web includes, but certainly is not limited
to…
-
Multi-URL
mega-databases that are too large for search engines to index
properly.
Here's a helpful list based on
category.
-
Records,
certificates, name directories, library indexes, etc.
-
Password-protected and members-only websites.
-
Timed access
pages. This could include the internal webpage for a test you're
taking for an online course.
-
Digital media
content that's blocked under a paywall. News organizations use
this as part of their revenue model to encourage readers/viewers
to subscribe and pay for journalistic reporting.
-
The back-end
dashboard of any sort of individual account, whether it be
banking, social platforms, email services, etc. This is only
available after an account is logged into and accessed. Then,
the URL changes to a private address accordingly.
-
Two-party
user-to-user communications or threads on social media, chat
services, messaging platforms, etc. The same rule for #4 applies
here.
The Deep Web is
extremely useful for communicating under encryption. These users
include anyone who needs protection from overseeing powers.
Below are some of
the main groups that benefit from the deep web's encrypted
communication capabilities:
1. Whistleblowers
and journalists

Edward Snowden is
the most well know whistleblower in recent times.
Intelligence
contractors, government or corporate employees, average citizens,
ex-spies, members of the military…these are all demographics that
have in the past opened up to journalists about corruption in their
fields.
Under the mask of
anonymity, they can communicate classified information to
journalists to expose the wrongdoings.
Prolific
whistleblowers like Edward Snowden and Chelsea Manning used this
route to share classified documents.
2. Free speech and
anti-censorship advocates, and political protesters

Anyone that seeks
to evade government surveillance (which, in many cases, could later
used to oppress free speech) finds the dark web a good place to
communicate anonymously.

The Deep Web also
comprises of websites and services that are specifically
gathered under the dark web category. This means they are
only accessible through Tor and they always end in .onion URLs.
Dark Web Markets
The dark web is
host to
hundreds of underground markets that sell all kinds of illicit
products and services, including…
1. Drugs

Dark web markets
sell every pharmaceutical product you can think of, from heroin to
mushrooms to LSD.
Most markets also sell legal prescription drugs,
ranging from ADHD medications to testosterone pills to even Prozac.

Stolen credit and
debit card details, social security numbers, and other such
information obtained through identity theft are often found on the
dark web.
3. Malware,
ransomware and hacking services

Hackers, phishing
experts, and ransomware and malware developers regularly advertise
their services on the dark web.
Cyber attacks are
on the rise over the last few years precisely because the act of
spreading ransomware is a lucrative practice for anyone who wants to
make money by holding data for ransom. There's also a recent spike
in adware campaigns.
These products and
services are often originally sourced from the dark web.
Ransomware
sales on darknet markets saw
an uptick of 2,502 percent in 2017 alone.
4. Weapons

Firearms, knives,
and even grenades and bomb equipment can be found on dark web
markets.
5. Hitman-for-hire
services

This particular
dark web market category entered into mainstream awareness after
Ross Ulbricht, founder of the infamous darknet market
Silk Road, was
arrested.
He was
eventually
sentenced to life imprisonment under charges relating to drugs,
hacking, money laundering and
procuring murder; the latter charge was particularly influential
in persuading the jury to convict Ulbricht of other charges in
addition to hiring a hitman to murder someone.
It's also what
gained the story international public attention among people
unfamiliar with the idea of darknet markets.
There are several
known markets that deal explicitly in the contracted assassin field
like
Hitman Network, for example.
Although, it is
worth noting that scammers will often use this "industry" to lure in
potential vulnerable victims and run off with their money without
getting the job done.
Child pornography
Unfortunately, the
cloak of anonymity brought by the Tor network also brings in rather
heavy share of pedophiles and predators - over 80 percent,
one study found.
Some darknet
platforms allow users to disseminate pornographic images and videos
of children, and some platforms even provide the means for users to
arrange meetings with their victims.
International law
enforcement have busted several such platforms within the last few
years, arresting thousands of child abusers and human traffickers in
the process. The number of users behind these sites are staggering.
One that
was busted by German law enforcement earlier this year, was
Elysium, which managed to reel in more than 87,000 users worldwide.
In 2014, the FBI
cracked down on Playpen, another child pornography site with 150,000
users.
The FBI apprehended
its creator and lead administrator, and proceeded to operate the
site to gather information on its users.
An investigation
followed that led to more than 800 U.S. and abroad arrests, and more
than 300 children being identified or rescued internationally.
Torrented content
Unreleased games,
movies and television shows galore are easy to come by on the dark
web. More sites are moving to the dark web in order to evade the
increasing threat of legal action over censorship or copyright
charges.
Leaked data dumps
This is a hot
category, at least dominating all headlines for months after a major
leak. There have been dozens of interesting leaks in the last five
years.
Here is a comprehensive and visually-compelling chart of them
all. Just a couple of the most notorious leaks include…
Adult Friend Finder
The Adult Friend
Finder breaches in
2015 and
2016 which collectively exposed the sexual preference data,
emails, usernames, IP addresses and login history of more than 303
million users of the hookup network.
Ashley Madison
An online dating
service that markets itself to people who want to cheat on their
spouses was hacked in July 2015.
After some months
of hesitation, the hacked data of around 32 million Ashley Madison
users was ultimately
released by the enigmatic hacking group
The Impact Team.
The
leak included names, phone numbers, addresses, member profiles,
as well as credit card details and records.
The Ashley Madison
leak was followed by
an exhaustive extortion campaign in which many victims of the
breach were tricked into paying scammers cash in exchange for
secrets that would supposedly damage their reputation.
There's an
excellent
TV documentary (Ashley
Madison Sex, Lies and Cyber Attacks) that chronicles how the Ashley Madison hack
unfolded, also detailing the subsequent scandals that blew up
afterwards.
WikiLeaks
Ever since the site
was created in 2006 by computer programmer and activist Julian Assange,
WikiLeaks data dumps have received massive public attention from
around the world.
It's worth a whole section but in the interest of
clarity, here's a snapshot of what the whistleblowing website
covers, plus examples in each category.
-
Intelligence: This series,
which is organized into sub-categories, gathers classified
information about the infrastructure, practices, policies
and implementations the intelligence industry and U.S.
government use to spy on citizens, foreign governments (even
allies) and intergovernmental departments.
-
Global Economy:
A range of detailed information pertaining to global high-stakes
topics, most recently including the
internal campaign emails of the 2017 French presidential
candidate Emmanuel Macron (who is now president).
-
International Politics:
Most prominent in this section is the
confidential reports leaked from the United Nations that
chronicle corrupt practices from sexual abuse to financial
fraud.
There's also an
email archive of the communications of Turkey's Justice and
Development party, documents about European Union-led
military operations regarding refugee boats, and more.
-
Corporations:
Inside the scandals and coverups involving major corporate
entities including a dossier about the infamous
Sony hack, records regarding global surveillance malware
vendor
Hacking Team, an archive of
taped material showing insight into a corruption scandal
involving two former U.S. presidents, and more.
-
Government:
This category broadly embroils all of the previous sections
combined.
-
War & Military:
Largely, this section is made up of documents, revelations,
reports and archives of classified U.S. military ops in Iraq and
Afghanistan.
There's also a trove of witness accounts and
records about the inner-practices of the U.S.'s nightmarish
detention facility in Guantanamo.
Facts & Tidbits
About the Deep Web
1. It enhances
privacy to a great extent

Encryption is
precisely the main function of the Deep Web. It is what defines it,
and it is what keeps it alive.
Because of the
solid layer of encryption offered by the Deep Web, it is regularly
utilized by individuals and groups that are vulnerable to
surveillance, hacks or other parties interested in compromising
their security.
This demographic
encompasses people such as journalists, whistleblowers, citizens
living under oppressive regimes riddled with censorship, and even
people who are in unsafe and abusive relationships who need a way to
communicate safely with others.
The Chinese
government has notoriously excessive censorship standards. So
notorious, in fact, that the rest of the world has taglined the
nickname,
The Great Firewall of China.
By utilizing the
deep web's encryption along with a private network or proxy, Chinese
citizens can bypass the firewall to access whatever content they
desire.
2. The Tor Onion
Router was created by the government

Interestingly, the
first individuals to think up a way to bypass the portal into
endless possibility was the United States government.
In the 1990s, a
team of Navy mathematicians crafted the Tor Onion Router technology
to allow military units and government agencies to communicate
classified material over an encrypted network.
This is the basis
for the dark web we know today
3. It comprises
most of the internet
Most estimates say
the Deep Web is made up of approximately 96 percent of the internet.
The smaller 4 percent is indexed by search engines like Google and
Bing.
Common
Misconceptions About the Deep Web
1. The Deep Web and
the dark web are the same
As is explained
above, the Deep Web and the dark web are entirely different, and
they both require special addresses to access the content found in
each case.
The Deep Web can be
accessed by a protocol that uses non-indexed web links, rather than
pages you can easily find through a Google Search.
By contrast, the
dark web is accessed using
the Tor browser. Links there operate
under a .onion domain.
2. It is only a
source of illegal goods and services
The Deep Web does
not entirely deal with illegal goods and services.
Because most of
the content on the Deep Web is mostly publically accessible with backends, indexes and data, it doesn't necessarily draw illegal
acts.
The dark web, however, is more of a haven for criminals.
Just because the
Deep Web is encrypted does not mean it's anonymous. It's entirely
probable for users' IP addresses and locations to be leaked.
The best mindset to
have is to assume that your information inevitably will be leaked
(even if the chance is low).
You're best
protected using
a Virtual Private Network (VPN) on the
Deep Web if you're doing
anything that's subject to any scrutiny, regardless of whether or
not it's legal.
This is just a smart security enhancement measure.
On the dark web in
particular, you should use a combination of Tor (to access .onion
sites) and VPN (to protect your anonymity and make your IP address
near-untraceable).
4. It's completely
secure
Similar to point
#3, it's important to assert that just because the Deep Web is
encrypted does not mean it's secure.
A good "What Not to
Do" case that's explicitly applied to the dark web can be made using
Silk Road creator Ross Ulbricht as an example.
The founder of the
notorious dark-net drug trade site
made a series of careless actions that eventually led the FBI to
his identity and location.
That said, people
can also be smart about running a dark-net market without getting
caught. It takes thinking ahead of law enforcement.
Dangers of the Deep
Web
1. Hackers

Hackers are ever at
bay wandering around on the deep and dark web, and they will seize
the opportunity to take advantage of an existing situation.
What's more is that
those who need some valuable information from a particular entity
will hire them to undertake various operations, such as obtain
confidential data or compromise a certain system to give desired
results.
Various confirmed
reports of data breaches and loss of funds due to hacking have been
reported in the recent past.
And the number of cases in which hacks
occur is ever-increasing.
2. Getting caught
for doing something illegal

Hundreds of people
have been caught and arrested by law enforcement for undertaking
illegal operations on deep and dark web.
Sometimes, these
people were in fact innocent; the government has a track record for
making examples out of people who were in the wrong place at the
wrong time - trying to send a message that they're serious about
crackdowns.
One such case
involved Barrett Brown, a journalist, activist and sort of press
office for the prolific hacktivism group, Anonymous.
Inside a thread in
Project PM, the online investigative community he founded, Brown
stumbled across a zipped file containing Stratfor data.
This was part of
the infamous Stratfor email hack of 2012, which leaked the global
intelligence firm's internal communications and client records to WikiLeaks who published it as part of its
Global Intelligence Files (GiFiles) leak.
Brown copied and
pasted that link of hacked data onto another forum so he and his
team could discuss its contents for a larger investigation about the
intelligence agency.
That's all he
did… copy and paste. Later, the feds arrested Brown and
charged him with possessing stolen content.
Several other
factors could expose your identity while on the Deep Web, such as
using your real name and email to post on forums. These tend to give
third parties a clue of who you are.
For this reason,
people can expose their identity without you even knowing it.
This would give
investigators enough time to monitor their activities and gather
sufficient evidence to incriminate them after an arrest.
3. Spying by ISPs
and the government.

For a fact, ISPs
(Internet Service Providers) can watch over every single detail
their customers are doing on the internet since they are offering
the service and have access to their systems' databases.
On the other hand,
governments possess the heavily-funded infrastructure and tools they
use to spy on their targets, many of whom are average everyday
citizens.
WikiLeaks has extensively compiled leaked secrets about
this deceptive practice.
Some of the leaks
have revealed that the Central Intelligence Agency (CIA) spies on
its targets by installing Trojans and malware that undertake various
types of operations.
The
WikiLeaks "Vault 7" dossier mentions how the CIA has developed
tools for each device that can access the internet and, as such, one
can be monitored without knowing.
Julian Assange and
WikiLeaks also found that
the CIA spies on its intergovernmental
counterparts, mainly the National security Agency (NSA).
4. Penalties and
legal issues.

Some countries have
strict guidelines that govern citizens' use of and behavior on the
internet.
Many of these
policies also extend to the hidden web, assuming users will
ultimately get caught evading the surface web. And as such, those
found violating the laws are subjected to penalties that include
fines or jail sentences.
With an increased
level of cybercrime, then such measures ought to be in place to
ensure that no one suffers at the expense of others.
Deep Web Anonymity - What Is It
and How to Achieve It
Staying anonymous
is imperative on the hidden web. Seeing as how
anonymity is one of its primary functions, why wouldn't you want
to do the best you can to achieve it?
Here are the main
programs you should download and guidelines you should follow to
stay anonymous on the deep and dark web:
1. Tor (The Onion
Router)

Tor has its origins
in the United States Naval Research Laboratory, where it was created
by
a team of mathematicians in the late 1990s to give the
government an extra layer of encryption in communicating sensitive
messages.
Its main
application was to protect intergovernmental communications and
intelligence information from being intercepted by foreign entities.
Today, the browser
is part of a larger open-source initiative called
The Tor Project, which is, in part, funded by the U.S.
Department of Defense.
It is tasked with
creating a series of programs to access and improve functions of The
Onion Router (Tor) network, which is what the Tor browser operates
through.
The Onion Router
network is an extremely unique technical invention. It is filled
with websites that end with a .onion domain, contrary to the
commonplace domain suffixes found on the surface web such as .com,
.org, .edu, and countless others.
The Tor browser
can be used to
access the surface web, the Deep Web and the dark web. And it's easy
to use since its interface and intuitiveness is nearly identical to
that of surface web-only browser Mozilla Firefox as the front end is clone of it.
But when you look
under the hood of how The Tor Browser actually works, its inner
functions are completely different.
When you use the
Tor browser, your connection bumps off a set of relays
run by volunteers from around the world on a distributed network
that extends from one end node to the other. The distributed nature
of the network is precisely what allows for the Tor browser to
protect your anonymity.
It attempts to
prevent your location and browsing habits from being picked up by
the sites you visit and communicate with.
So, The Tor Browser
has the ability to protect your anonymity in a superficial sense
(provided you don't register accounts on dark web sites with your
real name and sensitive information). But just because the Tor
network is mostly anonymous does not mean it's secure.
However, when using
the browser, a few measures ought to be taken to ensure that your IP
address is not leaked.
Among them is to
make sure that all other applications are closed and to keep the Tor
browser to its default size.
Other
guidelines ought to be followed to ensure that your privacy and
security is safeguarded while you're browsing through the dark web
in particular.
These guidelines
involve using a Virtual Private Network (VPN), which will give you
an extra boost in security as you navigate the dark web and also
give you a fail safe from
Tor vulnerabilities such as when it leaks your real IP, as it
has before.
2. Virtual Private
Networks

To further protect
yourself on the Deep Web, one should ensure that your
Virtual Private
Network is turned on even before launching the Tor browser since
it hides the actual location of an individual by changing their IP
address (which is usually used to track the location of a person) to
a random location on the globe.
For example, if
you're in Phoenix, Arizona and you want to browse the internet
freely (be it the surface web, dark web or the Deep Web), you can do
so by installing a trusty VPN and running it while you're online.
The VPN will mask
your real IP address (where you are, in Phoenix), and make it so
your IP address appears to be registered to a different, random
location anywhere in the world.
This way, anyone
who wants to find out your IP address will not be able to do so - your
IP address will appear to be registered in another location, like
Mexico City or Copenhagen or Toronto, and so on.
Furthermore, a VPN
will encrypt all of your information, sent and received, over the
internet or dark web.
This means that if someone could intercept it,
then they can not tell what you are doing anyway.
3. Pretty Good
Privacy (PGP) Encryption

Pretty Good Privacy
(PGP) is a communication system in which Important messages are
encrypted using the receiver's PGP encryption code.
When the message is
sent, the public key of the receiver is used, and then the receiver
uses their private key to decrypt the message.
The practice is
used in darknet markets where vendors and sellers use the encryption
method to protect the confidentiality of information they send
between each other.
The average
internet user may also find PGP useful for communicating online, as
the reality of government surveillance continues to loom over
citizens' everyday lives.
On a broader level,
PGP is used in instances where sensitive material is being exchanged
between two parties.
This includes
conversations about classified material between journalists and
whistleblowers, as well as intergovernmental communications between
federal entities.
Dark Web News has
published a comprehensive guide
here that outlines the importance of PGP and walks readers
through the process of setting one up.
4. Anonymous Email
Just as the name
suggests, anonymous email offers an individual increased online
privacy to a great extent.
Regardless of what
activities a person is pursuing on the Deep Web, they are always
recommended to
use an anonymous email in doing so.
That is, they should not use
their real email address, as it could easily disclose their identity
by revealing their name.
When creating the
email account, one should ensure that the username does not resemble
their actual name so as to avoid being subject to government
surveillance, fraud, scams, phishing attempts and other security
issues.
There are a number
of anonymous email services - most notably,
HideMyAss,
TorGuard and
Guerrilla Mail - you can try out if you'd like.
A full guide on
this topic has been made available by Dark Web News
here.
5. Passwords and
usernames

Among the blunders
that disclosed the real identity and ultimate arrest of former Silk
Road founder Ross William Ulbricht (alias "Dread Pirate Roberts")
was that
he used his real name and email address to post to public forums
about his activities on the dark web.
After this, it was
easy for the feds to track him down and arrest him.
This shows the
importance of using an anonymous username to undertake activities on
the Deep Web.
The use of strong
passwords is essential as well, as it ensures the account is not
easily compromised by not only hackers, but also close associates.
Strong passwords based on a given website will vary by meeting a
specific criterion.
But for starters, a
secure password should comprise of at least eight characters, have
words that are not found in the English dictionary, consist of at
least one uppercase letter, one number and special characters.
The general rule of
thumb is: the more complex the password, the more secure the
account. A simple
password manager program can help with this.
When it comes to
the username, it remains the responsibility of an individual to
ensure that it is not similar to their actual name just as in the
case of anonymous email handles.
6. Blocking the
Webcam

Hackers are ever at
bay and they're always ready to capitalize on any vulnerability
within a given system so that they can break into it.
One lucrative form
of ransomware attack is to take advantage of a computer's
vulnerability to install spyware that can take photos and videos via
the webcam, only to send the data directly to the hacker in real
time.
They can then
demand a ransom from you and, depending on the nature of the
photos/videos they capture with the webcam, chances are you'd be
even more incentivized to pay up the ransom.
An easy fix to this
is simply taping over your webcam or
covering it in some way so hackers won't be able to collect
visual records of your everyday life if your computer is compromised
This is a
frightening, but plausible possibility. It's no wonder why the CEO
of Facebook
has taped his webcam.
Deep Web Browsing
Tips
There are many
factors that compromise the online safety and security of a user
while on the Deep Web, despite the fact that you can just use a
regular browser to access it.
The average Joe
will probably leave more traces that reveal their identity as
compared to an expert who has been operating on the hidden web for
quite some time.
You'll get the hang
of it once you've had some time to get used to the Deep Web, but
below are just a few best practices to keep in mind for your safety.
(Note that all
of these tips apply to both the dark web and the Deep Web. The only
difference is that you cannot access the dark web without using the
Tor browser, as you will not be able to reach .onion links on a
regular browser.)
Practice safe
clicking

Avoid all malicious
links that aren't sourced from a trusted website or user.
If you're browsing
the dark web in particular, you should always ALWAYS double check
and even triple check to make sure you're using the current .onion
URL for whatever site you intend to visit.
Dark web links are
constantly susceptible to change, so it's best you check with a
reputable source to make sure the link is verified.
Watch what you
download

Don't download
applications, .pdf's, or anything from untrusted sources or
websites. It's as simple as that.
Get an
up-to-date antivirus program

The devices used to
access the hidden web should be clean and have an up-to-date
antivirus that ensures their computer is not contaminated.
Hackers will often
infiltrate a device by installing spyware on the browsers the
victims are using. By doing so, information about the user's
activities is sent to the spyware developer in real-time.
Connect to
trusted networks

Last but not least,
don't ever connect to unsecure or unknown networks. This includes
the Wi-Fi at your friendly cyber cafe or coffee shop.
Sometimes it's
best to just use a network you trust.
Deep Web Sites and
.Onion Links
The dark and Deep
Web are filled with interesting content of all different categories.
Dark web links are followed by a .onion parameter, and Deep Web
links could contain any other domain.
Here are tables
containing the top 10 most popular sites on both the dark and Deep
Web, along with corresponding links.
Dark Web News has
compiled the biggest source of
Deep Web links and
screenshots online, and it's continuously growing.
Deep Web
Screenshots
Real-time or recent
screen captures of live Deep Web sites are incredibly useful for
anyone who's thinking about exploring on the Deep Web.
Screenshots give
you a chance to take a peek into the website and its potential
offerings without having to visit it yet.
Once you've decided
it's worth the dive, you can enter the site at the correct link
associated with the screenshot. Dark Web News has
the largest selection of screenshots on the surface web.
If you head over to
this page,
then you can click on the eye symbol for any record in the table to
view the screenshot of the site.
Deep Web Search
Engines & Tools
The Deep Web does
not have Google because of its prime characteristic of having data
that is not indexed. This might sound like a disadvantage given the
fact that Google has spoiled us all with easy and quick search
returns.
But it's imperative
to remember that the entire purpose of the Deep Web is that it's an
open source of information that anyone is welcome to take stock in,
and it has much MUCH more to offer than any Google search.
You just have to
know how to harness the Deep Web to your advantage.
There are some
search engines made for use in the dark web, and one of them is
GRAMs,
which happens to be the very first search engine of its kind to be
developed to browse through the Tor network.
Due to the rising
number of darknet markets, the developers saw the need to create a
search engine that is convenient for dark web users.
It enables them to
search the Tor network for markets, and it also provides guides for
purchases and sales.
Some other
alternative search engines and tools for finding and consuming
content on the deep and dark web include:
-
DuckDuckGo:
This is an anonymous search engine that keeps no logs of users'
browsing behaviors, search results, history, cookies, etc.
It's
mainly used for browsing the surface web in a more anonymous
way, but it picks up Deep Web links too.
-
Torch (xmh57jrzrnw6insl.onion
- you have to use
TOR search engine to see
this content):
With over 10 million users and years of positive
reputation-building under its belt, Torch has gained notoriety
among the deep and dark web communities for delivering high
quality search services of the hidden internet.
It's based on
the Chromium suite and is compatible with Chrome extensions and
add-ons.
-
Uncensored
Hidden Wiki (zqktlwi4fecvo6ri.onion/wiki/index.php/Main_Page
- you have to use TOR search engine to see this content):
The oldest and truest form of dark web search mastery is the
Hidden Wiki.
It is a repository for links to all sorts of
websites on the darknet, from drug markets to fanbases to
uncensored news publications to even some darker content having
to do with human trafficking and abuse.
That's why you should be
careful what you click on when you scroll through the Hidden
Wiki; it certainly doesn't discriminate on what graphic content
is on the list.
-
The WWW Virtual Library
is the oldest and most vast catalog of internet websites of all
time.
It was created
at the European Organization for Nuclear Research by the
founder of the World Wide Web and HTML himself, Tim Berners-Lee.
The database has educational and encyclopedic references on
virtually any topic thinkable.
-
This list
has some additional search engines you can try out based on your
needs.
-
Ichidian:
A launched recently search engine helps users access dark web
URLs in a faster and easier manner than others. It's new, so it
may take some time to adjust to its new user base.
-
notEvil (hss3uro2hsxfogfq.onion
- you have to use TOR search engine to see this content):
This is also an in-depth list of deep and dark web links. notEvil has been around for some time, and is widely known among
the community as a good source for links.
Deep Web Reddit
Resources

Reddit is a major
source of information about Deep Web topics.
Subreddit forums offer
Deep Web users the opportunity to freely express themselves on
various issues, obtaining first-hand information on anything that
concerns the deep and dark web.
However, since the
main function of Reddit is to be a tool for expressing uncensored
views and opinions, deep/dark web forums on Reddit have indeed
landed people into trouble with law enforcement since some tend to
overshare and use their real names to post comments about their
practices.
Users in dark/Deep
Web subreddit communities can sometimes be at odds with each other.
If you're just an average onlooker, you'll find the whole culture
behind this scene incredibly fascinating to watch.
Users are downright
combative with one another on a regular basis; sometimes comedically
so. But that's the way of life within this niche. Trolling is not
only tolerated, it's accepted.
Hackers will often
openly brag about their exploits and taunt others for not being able
to meet the challenge due to their "lower" skill sets.
As a result, angry
fellow commenters may be motivated to dox that user. This happened
recently with
a user
named PhishKingz, a phishing guru of sorts who has been behind
some of the dark web's notable phishing campaigns.
Many of those who
engage in fraud and illegal activities end up exposing their
identity to some extent.
Additionally, some
darknet market users, admins, vendors and buyers tend to end up
getting caught for accidentally exposing their identity.
And as a result,
investigative bodies and law enforcement agencies monitor the
subreddit forums for any leads of persons that may be engaging in
criminal actives.
Consequently, this
has over time led to the rest of quite a number of people.
For this reason,
those posting on Reddit should ensure that they have turned on their
VPN before logging into their account (creates with an anonymous
email) and posting.
Failure to do so
could lead to the actual IP address of the user getting exposed,
making it easier to get traced.
Other measures
include use of fake email addresses for making Reddit accounts, as
well as fake usernames. The username should no way resemble the
actual name or identity of the person.
Below are some of
the sub-reddit forums that relate to the Deep Web:
Deep Web
-
https://www.reddit.com/r/deepweb
shares verifiable tools, resources and general information that Deep
Web users find interesting and helpful.
-
https://www.reddit.com/r/DeepWebTopics
is a topical discussion board where users posts, stories, questions,
observations and comments about things they've seen or want to see
on the Deep Web.
-
https://www.reddit.com/r/DeepWebIntel
is a general forum for Deep Web users to communicate, created by a
user of the same name.
-
https://www.reddit.com/r/onions
is more dark web-related, but it's a helpful source for finding out
more about what the darknet has to offer.
-
https://www.reddit.com/r/deepwebexperiences
is a spot where people can share some of the interesting things
they've seen on the Deep Web.
-
https://www.reddit.com/r/WikiLeaks,
https://www.reddit.com/r/WikiLeaksDiscussions (invite-only) and
https://www.reddit.com/r/WikileaksTaskForce are all dedicated to
free and open conversation around WikiLeaks, Julian Assange and
whistleblowing in general.
-
https://www.reddit.com/r/DeepWebMysteries/
is a community of citizen investigators who look for hidden meanings
and patterns in Deep Web sites. It's invite-only, so you have to
message the moderators to get access to the subreddit.
-
https://www.reddit.com/r/deepwebpics
is exactly what it sounds like - a bunch of screenshots from Deep
Web
sites, or screenshots depicting content that's related to the Deep
Web in some way.
Carding
Dark Net Markets
-
https://www.reddit.com/r/DarkNetMarkets2
is definitively the most widely used subreddit for dark web market
vendors, buyers, admins, observers and browsers to communicate and
swap tips and information about the associated darknet market
brands.
-
https://www.reddit.com/r/DNMAvengers
compiles an index of tested products from confirmed darknet market
buyers, in a bid to add more accountability to the scene; the
subreddit is currently under construction, but it's still accepting
new submissions.
Hacking
-
https://www.reddit.com/r/hacking
is a subreddit for anyone in the hacking community, whether it be
full-time hackers, curious users who want to tip their toes into the
vice, or onlookers who simply enjoy reading countless threads of
hacker culture on Reddit.
-
https://www.reddit.com/r/Hacking_Tutorials
is a peer-to-peer educational subreddit for methods, tools,
resources and tips hackers can use to carry out their activities.
-
https://www.reddit.com/r/hackingwithswift
is a place where iOS and Swift developers and hackers can post
questions/answers, swap comments and suggestions, and share cool
projects with one another.
Deep Web Horror
Stories
The number of
creepy stories about the invisible web as of now is endless. And
what's more is that these numbers grow day by day.
Red Rooms
As its name
suggests, "Red Rooms" are places where people are brutally
slaughtered on camera for anyone inside the chat room to watch from
home.
Due to the fact
that most witnesses of this phenomena only have their experience and
memory to use as evidence, there have been several rumors that Red
Rooms are actually a hoax.
Observers have
claimed that the sites will offer a "Pay Per View" button where
users provide payment in Bitcoins to gain access to watch the
content.
If Red Rooms are to
be believed as true, they'd be best described as live-streamed snuff
films, formatted for the Internet Age. Or, they could very well be
just a twisted scam.
Human Experiments
As scary as it
sounds, this is indeed something that occurs in the dark web.
There is an
enigmatic site called The Human Experiment, run by a group that
abducts human beings and performs a whole host of experiments on
them just for fun.
The acts performed
on humans include starvation, radiation exposure, injecting
chemicals into the body, among many others.
Sexual Content
Some of the content
found on the Deep Web is highly explicit, and the scenes are not
worth exploring especially for the faint-hearted.
Abductions and
kidnapping for sexual purposes have been long documented on various
dark web sites.
There have been
numerous accounts and stories of innocent wanderers of the dark web
(usually newbies to the scene) who accidentally stumble upon this
type of content. As a result, they're emotionally scarred for a long
while afterwards, or even indefinitely.
The dark web is
often host to content that depicts humans performing acts of
bestiality on animals and engaging minors in sexual acts.
The price for these
videos or photos depends on the site but on some occasions, the
content is available to download for free.
Viewing this type
of content is illegal in almost all countries and Dark Web News do
not condone it at all. We are just reporting on what is actually
found here.
Summoning Demons
Very crazy, right?
But it is indeed a vice that many are performing.
These sites are
formed by members of cults who engage each other by showing bizarre
rituals, such as eating human flesh and drinking human blood in the
act of offering sacrifices.
Creepy Games
There are some
seriously dark games that are floating around the dark web right
now.
One such example is
the Blue Whale Suicide Challenge, which
is loosely linked to around 130 deaths of teenagers throughout
Russia as of September 2017 (because of ongoing investigations, that
link has yet to be proven definitively).
The games starts
off by trying to get the player addicted to it over a time period of
50 days by rewarding them for completing challenges that range in
severity, from watching scary movies to physically hurting
themselves.
The more the user
plays the game and goes through more advanced levels, the more
challenges they're required to solve.
At the end, the game tasks
them with committing suicide.
Deep Web Torrent
Sites
Perhaps it goes
without saying, but extreme caution is absolutely required when
undertaking any sort of torrenting activity.
Torrenting on the
surface web can be dangerous, as your IP address and browsing
history are readily made available to your Internet Service Provider
(ISP).
Entertainment
producers are incredibly touchy about their copyrighted content so,
to avoid legal action, it's best to use torrent sites under the
cloak of anonymity on the Deep Web - using the Tor browser or
I2P,
another network that serves to protect users' privacy.
Here's a
plug to Dark Web News'
in-depth Tor guide, which can help get you started.
Here's a rundown of
some of the most reliable torrenting platforms, and their
corresponding links:
The
Pirate Bay -
uj3wazyk5u4hnvtk.onion

TPB is one of the
most popular and all-inclusive torrent platforms that's dominated
the scene since its start in 2003.
The surface web site is
periodically subject to domain seizures, but the Tor version has
remained intact.

As its name states,
Solarmovie is a searchable database of movies. It covers pretty much
every genre you can think of.

This is a
longstanding BitTorrent-enabled discussion forum that facilitates
peer-to-peer file sharing.
The surface web address is:
demonoid.pw.
BTDB

Standing for
BitTorrent Database, BTDB is a search engine for searching nodes
that distribute torrent files via the BitTorrent file sharing
protocol.
There doesn't appear to be a .onion link for this one, but
it's accessible via the surface web
here.
Wrap Up
The Deep Web is a
fascinating place to be for any internet denizen.
It's a rabbit hole
of internet wonder, offering all sorts of knowledge, records, data
and content a person could spend days sifting through.
It may take a few
steps to navigate your way through the various links and virtual
pathways to find the insights you're looking for, but that's all
part of the fun.
The Deep Web is
beckoning your entrance.
And if you're up for the task, you might
find the answers you've been looking for within its depths.
|



































