
by Glenn Greenwald and Ewen MacAskill
7 June 2013
from
TheGuardian Website
• Top-secret Prism program claims
direct access to servers of firms including Google, Apple and
Facebook
• Companies deny any knowledge of program in operation since
2007
• Obama orders US to draw up overseas target list for
cyber-attacks

A slide depicting the
top-secret PRISM program.
Origin
The
National Security Agency (NSA) has
obtained direct access to the systems of Google, Facebook, Apple and other
US internet giants, according to a top secret document obtained by the
Guardian.
The NSA access is part of a previously
undisclosed program called Prism, which
allows officials to collect material including search history, the content
of emails, file transfers and live chats, the document says.
The Guardian has verified the authenticity of the document, a 41-slide
PowerPoint presentation - classified as top secret with no distribution to
foreign allies - which was apparently used to train intelligence operatives
on the capabilities of the program.
The document claims "collection directly from
the servers" of major US service providers.
Although the presentation claims the program is run with the assistance of
the companies, all those who responded to a Guardian request for comment on
Thursday denied knowledge of any such program.
In a statement, Google said:
"Google cares deeply about the security of
our users' data. We disclose user data to government in accordance with
the law, and we review all such requests carefully.
From time to time, people allege that we
have created a government 'back door' into our systems, but Google does
not have a back door for the government to access private user data."
Several senior tech executives insisted that
they had no knowledge of Prism or of any similar scheme.
They said they
would never have been involved in such a program.
"If they are doing this, they are doing it
without our knowledge," one said.
An Apple spokesman said it had "never heard" of
Prism.
The NSA access was enabled by changes to US surveillance law introduced
under Bush and renewed
under
Obama in December 2012.

The program facilitates extensive, in-depth surveillance on live
communications and stored information.
The law allows for the targeting of any
customers of participating firms who live outside the US, or those Americans
whose communications include people outside the US.
It also opens the possibility of communications made entirely within the US
being collected without warrants.
Disclosure of the Prism program follows a leak to the Guardian on Wednesday
of a top-secret court order compelling telecoms provider Verizon to turn
over the telephone records of millions of US customers.
The participation of the internet companies in Prism will add to the debate,
ignited by the Verizon revelation, about the scale of surveillance by the
intelligence services. Unlike the collection of those call records, this
surveillance can include the content of communications and not just the
metadata.
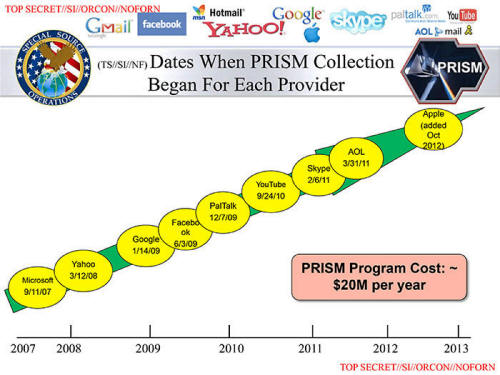
Some of the world's largest internet brands are claimed to be part of the
information-sharing program since its introduction in 2007.
Microsoft - which is currently running an
advertising campaign with the slogan "Your privacy is our priority" - was
the first, with collection beginning in December 2007.
It was followed by,
-
Yahoo in 2008
-
Google, Facebook and PalTalk in 2009
-
YouTube in 2010
-
Skype and AOL in 2011
-
finally Apple, which joined the program
in 2012
The program is continuing to expand, with other
providers due to come online.
Collectively, the companies cover the vast majority of online email, search,
video and communications networks.
Origin
The extent and nature of the data collected from each company varies.
Companies are legally obliged to comply with requests for users'
communications under US law, but the Prism program allows the intelligence
services direct access to the companies' servers.
The NSA document notes the operations have,
"assistance of communications providers in
the US".
The revelation also supports concerns raised by
several US senators during the renewal of the
Fisa Amendments Act in December 2012, who
warned about the scale of surveillance the law might enable, and
shortcomings in the safeguards it introduces.
When the FAA was first enacted, defenders of the statute argued that a
significant check on abuse would be the NSA's inability to obtain electronic
communications without the consent of the telecom and internet companies
that control the data. But the Prism program renders that consent
unnecessary, as it allows the agency to directly and unilaterally seize the
communications off the companies' servers.
A chart prepared by the NSA, contained within the top-secret document
obtained by the Guardian, underscores the breadth of the data it is able to
obtain:
email, video and voice chat, videos, photos,
voice-over-IP (Skype, for example) chats, file transfers, social
networking details, and more.

Origin
The document is recent, dating to April 2013.
Such a leak is extremely rare
in the history of the NSA, which prides itself on maintaining a high level
of secrecy.
The Prism program allows the NSA, the world's largest surveillance
organization, to obtain targeted communications without having to request
them from the service providers and without having to obtain individual
court orders.
With this program, the NSA is able to reach directly into the servers of the
participating companies and obtain both stored communications as well as
perform real-time collection on targeted users.
The presentation claims Prism was introduced to overcome what the NSA
regarded as shortcomings of Fisa warrants in tracking suspected foreign
terrorists. It noted that the US has a "home-field advantage" due to housing
much of the internet's architecture.
But the presentation claimed "Fisa constraints
restricted our home-field advantage" because Fisa required individual
warrants and confirmations that both the sender and receiver of a
communication were outside the US.
"Fisa was broken because it provided privacy
protections to people who were not entitled to them," the presentation
claimed.
"It took a Fisa court order to collect on
foreigners overseas who were communicating with other foreigners
overseas simply because the government was collecting off a wire in the
United States. There were too many email accounts to be practical to
seek Fisas for all."
The new measures introduced in the FAA redefines
"electronic surveillance" to exclude anyone "reasonably believed" to be
outside the USA - a technical change which reduces the bar to initiating
surveillance.
The act also gives the director of national intelligence and the attorney
general power to permit obtaining intelligence information, and indemnifies
internet companies against any actions arising as a result of co-operating
with authorities' requests.
In short, where previously the NSA needed individual authorizations, and
confirmation that all parties were outside the USA, they now need only
reasonable suspicion that one of the parties was outside the country at the
time of the records were collected by the NSA.
The document also shows the FBI acts as an intermediary between other
agencies and the tech companies, and stresses its reliance on the
participation of US internet firms, claiming "access is 100% dependent on
ISP provisioning".
In the document, the NSA hails the Prism program as,
"one of the most valuable, unique and
productive accesses for NSA".
It boasts of what it calls "strong growth" in
its use of the Prism program to obtain communications.
The document highlights the number of obtained
communications increased in 2012 by 248%
for Skype - leading the notes to remark there was,
"exponential growth in Skype reporting;
looks like the word is getting out about our capability against Skype".
There was also a 131% increase in requests for
Facebook data, and 63% for Google.
The NSA document indicates that it is planning to add Dropbox as a PRISM
provider.
The agency also seeks, in its words, to,
"expand collection services from existing
providers".
The revelations echo fears raised on the Senate
floor last year during the expedited debate on the renewal of the FAA powers
which underpin the PRISM program, which occurred just days before the act
expired.
Senator Christopher Coons of Delaware specifically warned that the
secrecy surrounding the various surveillance programs meant there was no way
to know if safeguards within the act were working.
"The problem is: we here in the Senate and
the citizens we represent don't know how well any of these safeguards
actually work," he said.
"The law doesn't forbid purely domestic information from being
collected. We know that at least one Fisa court has ruled that the
surveillance program violated the law. Why? Those who know can't say and
average Americans can't know."
Other senators also raised concerns. Senator
Ron Wyden of Oregon attempted, without success, to find out any
information on how many phone calls or emails had been intercepted under the
program.
When the law was enacted, defenders of the FAA argued that a significant
check on abuse would be the NSA's inability to obtain electronic
communications without the consent of the telecom and internet companies
that control the data. But the Prism program renders that consent
unnecessary, as it allows the agency to directly and unilaterally seize the
communications off the companies' servers.
When the NSA reviews a communication it believes merits further
investigation, it issues what it calls a "report".
According to the NSA,
"over 2,000 Prism-based reports" are now
issued every month.
There were 24,005 in 2012, a 27% increase on the
previous year.
In total, more than 77,000 intelligence reports have cited the PRISM
program.
Jameel Jaffer, director of the ACLU's Center for Democracy,
that it was astonishing the NSA would even ask technology companies to grant
direct access to user data.
"It's shocking enough just that the NSA is
asking companies to do this," he said.
"The NSA is part of the military. The
military has been granted unprecedented access to civilian
communications.
"This is unprecedented militarization of domestic communications
infrastructure. That's profoundly troubling to anyone who is concerned
about that separation."
A senior administration official said in a
statement:
"The Guardian and Washington Post articles
refer to collection of communications pursuant to Section 702 of the
Foreign Intelligence Surveillance Act. This law does not allow the
targeting of any US citizen or of any person located within the United
States.
"The program is subject to oversight by the Foreign Intelligence
Surveillance Court, the Executive Branch, and Congress. It involves
extensive procedures, specifically approved by the court, to ensure that
only non-US persons outside the US are targeted, and that minimize the
acquisition, retention and dissemination of incidentally acquired
information about US persons.
"This program was recently reauthorized by Congress after extensive
hearings and debate.
"Information collected under this program is among the most important
and valuable intelligence information we collect, and is used to protect
our nation from a wide variety of threats.
"The Government may only use Section 702 to acquire foreign intelligence
information, which is specifically, and narrowly, defined in the Foreign
Intelligence Surveillance Act. This requirement applies across the
board, regardless of the nationality of the target."
NSA leak
Source believes exposure, consequences inevitable
PRISM’s Breaking
by Tyler Bass
June 9, 2013
from
Chronicle Website
WASHINGTON
Last week the National Security Agency’s newly
uncovered PRISM surveillance program, intended to manager foreign
intelligence from electronic service providers, elicited anger that millions
of Americans’ communications had been swept up in a comprehensive dragnet.
News of the PRISM program came at the end of a
breakneck week of national security
reporting at The Guardian, where columnist Glenn Greenwald
took a step from his legacy of punditry and opinion-oriented content to
reporting.
The Guardian
and The Washington Post, who both revealed the
existence of the PRISM program Thursday, declined to release all 41 slides
of the top-secret PowerPoint presentation they had obtained.
Barton Gellman, co-author of the
Washington Post story, told The Internet Chronicle Friday,
“We put up the [slides] we thought we
should. Much of the document seemed to us to be classified for good
reason. We’re not engaged in a mindless,
indiscriminate document dump, and our source didn’t want us to be,”
Greenwald
told Buzzfeed Saturday.
“We’re engaged in the standard journalistic
assessment of whether the public value to publication outweighs any
harms.”
In
a statement released in response to massive public outcry, Google CEO
Larry Page was adamant that the company has not granted the NSA any
“back door” to his company’s servers, adding that Google had not heard of
any program called PRISM until Thursday.
However an additional slide in a top-secret
PowerPoint presentation, fed to The Guardian and
annotated by reporter James Ball, suggested that the PRISM
program enabled data “collection directly from the servers of… Google,”
among other computing giants, such as Microsoft and Yahoo!
In accordance with Gellman and Greenwald’s
claims to the press, some of this additional slide is blacked out.
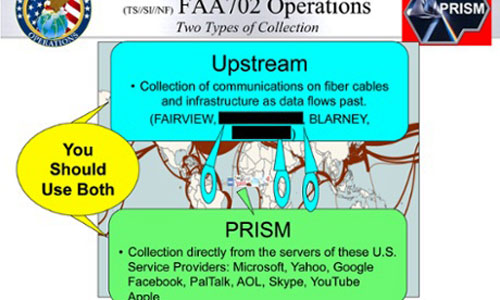
NSA
PRISM PowerPoint presentation slide suggesting
“direct collection”
from U.S. service providers’ servers.
(Cropped slide via
The Guardian)
People briefed on the negotiations between the
media giants - speaking anonymously, as law prohibits them from
acknowledging the very “existence” of Foreign Intelligence Surveillance Act
requests - seemingly expanded on Page’s claims on Friday.
It was then that The New York Times‘
Claire Cain Miller relayed her sources’
claims
that, in the cases of Facebook and Google, some consensus had
been reached between corporate and public partners on the construction of
digital drop boxes, intermediary locations where the corporations would not
offer carte blanche to the NSA but - after having in-house
attorneys review government requests - they could leave requested
information.
“[T]he government would request data,” wrote
Miller, “companies would deposit it and the government would retrieve
it.”
Earlier last week government officials and
politicians finally came clean about vast collection by the NSA of millions
of Americans’ telephonic metadata.
The telephone metadata - or logs of involved
telephone numbers and call lengths - was turned over by Verizon, the
telephone provider for a plurality of citizens. That revelation, and
subsequent admissions, flies in the face of several statement by public
officials.
Among those statements is one by NSA Director
and Army Lt. Gen. Keith Alexander at the Washington-based American
Enterprise Institute in July of 2012.
Replying to a question from Fox News Channel’s
Catherine Herridge, Alexander said,
“We don’t hold data on U.S. citizens.”
See the full interview:
Cyber Security and American Power
(above clip at 42:48)
During a March 12 Senate Intelligence Committee
hearing, Sen. Ron Wyden (D-Ore.) asked National Intelligence Director
James Clapper about the scale of any NSA dragnet.
Fast-forward to 6:42 in the video, following,
for this exchange.
Ron Wyden: Does the NSA collect any type of
data at all on millions or hundreds of millions of Americans?
James Clapper: Clapper: No, sir.
Wyden: It does not?
Clapper: Not wittingly. There are cases
where they could inadvertently perhaps collect but not wittingly.
On May 4, 2012, Sens. Wyden and Mark
Udall (D-Colo.) sent a letter asking the NSA inspector general, I.
Charles McCullough,
“how many people inside the United States
have had their communications collected or reviewed.” McCullough replied
in his own letter that “an [inspector general] review of [that] sort
suggested would violate the privacy of U.S. persons.”
In 2007, then Senator Barack Obama
(D-Ill.) expressed outrage that the Bush administration had engaged in
spying “on citizens who are not suspected of a crime.”
Critics of the Obama administration have claimed
that this amounts to hypocrisy on the part of the president.
During a March 2012 hearing of the Emerging
Threats and Capabilities Subcommittee of the Armed Services Committee,
Representative Hank Johnson (R-Ga.) asked Alexander if the NSA
routinely intercepts American citizens’ emails, to which Director Alexander
replied, “No.”
Video follows.
The Washington Post
however reported Friday that, from PRISM’s Web terminal at NSA Headquarters
at Fort Meade, Md., NSA analysts key in “selectors” intended to determine
with at least half accuracy a given target’s “foreignness.”
The Post obtained analyst training
materials that specifically address how analysts are to report any given
“accidental” collection, but those materials add that that collection on
citizens is "nothing
to worry about."
On Saturday Atlantic staff writer
Conor Friedersdorf
raised troubling questions about the implications of the NSA’s newly
revealed and utterly vast collection of telephone metadata and “incidental”
private, domestic media content.
Even assuming the best of intentions and utmost
integrity out of domestic law enforcement, should a foreign government make
its way into NSA databases, he wrote, that,
“could enable blackmail on a massive scale,
widespread manipulation of U.S. politics, industrial espionage against
American businesses;, [sic] and other mischief I can’t even imagine.”
Added Friedersdorf:
“What if [China, Russia, Pakistan, Iran,
Saudi Arabia or a successor to al-Qaeda] breached the database’s
security without our even knowing?”
Claims of 'Lives Saved'
by the Surveillance Panopticon
A “U.S. intelligence official,” speaking on
condition of anonymity to CBS News,
said that the PRISM program “thwarted” a 2009 attempt to bomb the New
York City subway system, an attack that could have killed hundreds of
people.
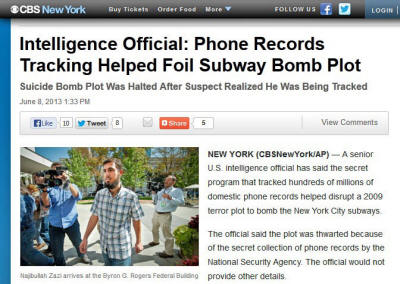
CBS News claims:
“Suicide Bomb Plot Was Halted
After Suspect Realized He Was Being Tracked”
“U.S. government sources”
made similar statements to Reuters’ Mark Hosenball Friday.
Hosenball’s source addressed statements Tuesday
afternoon by House Intelligence Committee Chairman Mike Rogers (R-Mich.),
although the Guardian and Washington Post stories that
broke the existence of PRISM were not released until that evening.
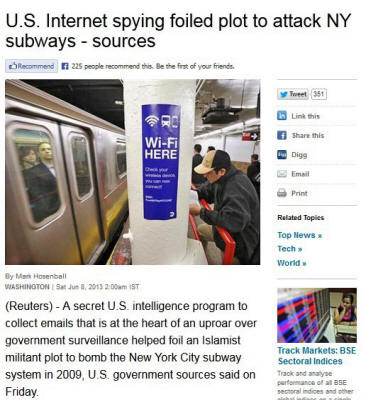
“The surveillance program
that halted the Zazi plot
was one that collected email
data on foreign intelligence suspects,”
a government source told
Reuters.
The New York Times
similarly
reported on Friday that PRISM “yielded concrete information.”
The Times‘ Eric Schmitt,
David Sanger and Charlie Savage, relying on an anonymous “senior
intelligence official” source, wrote Friday that a September 2009 email from
an address “being monitored by the vast computers controlled by American
intelligence analysts” allowed the analysts to locate the would-be bomber in
Aurora, Colo.
The anonymous intelligence official added that
Zazi was located,
“through an e-mail correspondence that we
had access to only through” PRISM.







