|
(Nov-Dec 2019) from NewDawnMagazine Website
Power is a peculiar thing. In different ways, we've become accustomed to co-existing with it and will even forgo some liberties as part of a Faustian trade-off for various modern conveniences.
When that power is virtually invisible, it is beyond scrutiny; and when it's transnational, it takes on a whole new dimension.
We are now fast
approaching a point in history where opaque structures of power pose
a direct threat to our hard-fought-for constitutional and democratic
institutions.
He revealed what could only be described as a vast international conspiracy, in which multiple Western intelligence agencies work hand-in-hand collecting and analyzing the personal data of their citizens, completely side-skirting any domestic laws guarding our right to privacy and due process.
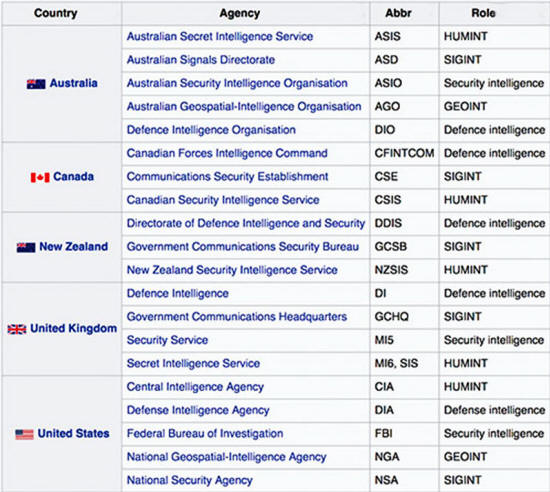
This 'conspiracy' plays a pivotal role in backing-up various allied deep states around the world. The operational core of this digital syndicate is known as the Five Eyes alliance.
Code named FVEY, it represents an international signals intelligence (SIGINT) and communications intelligence (COMINT) gathering agreement between,
The Five Eyes alliance agencies include, but are not limited to,
This cooperative intelligence-sharing arrangement traces its
historical roots to the
UKUSA Agreement of 1946, as generally
agreed in the 1941 Atlantic Treaty signed between the Allied powers
during World War Two.
These include spying agencies from,
The Nine Eyes would later expand to a Fourteen Eyes agreement which includes the Nine Eyes plus,
Not surprisingly, the Fourteen Eyes more or less corresponds with the core European members in the NATO military alliance.
The Fourteen Eyes may also be extended up to 17 Eyes when considering other regular third party contributors like,
Initially, the Five Eyes arrangement was ideally suited for the Cold War where the primary task was gathering intelligence from the former Soviet bloc countries and their allies.
Later, as the internet expanded, the sheer volume of digital content and communications meant that the Five Eyes had to readjust its core competency - from an organization mainly preoccupied with spying on governments, institutions, and persons of interest, to an organization whose primary task was to spy on absolutely everyone.
With this new raison d'ętre in mind, the Five Eyes cooperative framework became ideal for allowing spy agencies to bypass domestic laws that might prohibit them from conducting surveillance or hacking their country's own citizens.
Overcoming legal or technical barriers became fairly straightforward, especially in the wake of the attacks of 9/11.
The
USA Patriot Act
meant that intelligence and law enforcement agencies could invoke
national security and require telecoms companies and internet
service providers (ISPs) to allow fiber optic splitters to be
installed at key nodes in the telecommunications infrastructure,
allowing spooks to divert massive data flows to be captured and run
through the various Five Eyes data analysis centers.
The participating intelligence agencies
of each country in the 5 Eyes alliance.
Once they reached this stage, getting it to perform was simply a case of tweaking the software.
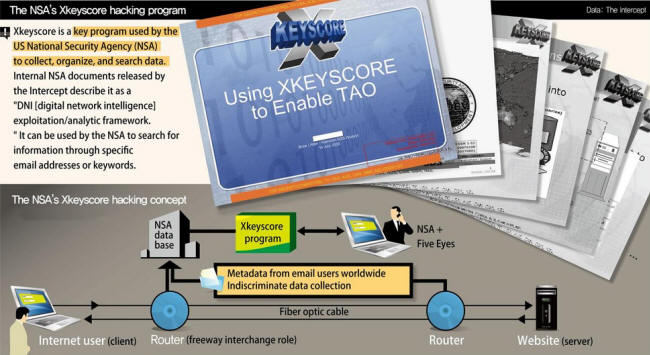
When Snowden's story broke in 2013, one of the key components of the NSA's mass surveillance operation was a software interface called XKEYSCORE.
The Intercept describes the tool as follows:
Whereas previous iterations of the NSA's global information dragnet hauled in large quantities of data and required a combination of computer and human intelligence to sift through it all, XKEYSCORE,
In essence, what used to be done by the entire ECHELON system and scores of human analysts could now be achieved with a few strokes of the keyboard.
Imagine if the NSA connected all of these data trawling nodes with an artificial intelligence backbone that analyzed and parsed out teraflops of information in real-time.
It would make the agency omnipotent. This very same dystopian scene was brought to life on the big screen in the 2015 James Bond film Spectre starring Daniel Craig.
In the film, a latter-day Blofeld, played by actor Christoph Waltz, devised a new unofficial international ruling committee, S.P.E.C.T.R.E. (Special Executive for Counter-intelligence, Terrorism, Revenge and Extortion), comprised of the world's top organised crime figures.
Through his network's infiltration of the very top levels of Western intelligence, Blofeld receives unrestricted, real-time access to all surveillance data collected by the "Nine Eyes" countries.
This backdoor key gives
Blofeld the power to steer global political events, move markets,
and when necessary, blackmail any individual or institution into
compliance.
Even without Blofeld, the current Nine Eyes intergovernmental network retains all of the capabilities that any nefarious villain would ever want, to wield power or ward off any potential challengers.
If operations are conducted outside public view, then the potential for abuse is virtually boundless.
Blofeld wasn't wrong. In essence, the Five Eyes intelligence network is precisely that - a type of Anglo-fraternal organization that wields a noticeable advantage over its rivals.
Such unfettered cooperation between advanced nations like the US, UK, Canada, Australia and New Zealand, means that the technical continuity of this geopolitical alliance remains more or less unmatched.
Leveraging the resources
of five countries spread around the globe affords the coalition a
substantive advantage over just about any other global competitor.
No other bloc can match its scope and scale, geographically and
technologically.
The fact that this network comprises current and former British colonial possessions speaks to the Anglo-centric or Atlanticist worldview on which its mission is based.
That Atlanticist agenda
is best described as something akin to a
Bilderberg Committee agenda - a set
of political and industrial objectives and goals informally agreed
upon by some of Western society's most powerful luminaries and
technocrats who meet at the beginning of summer at the annual Bilderberg Meeting.
While German spy agencies like the Bundesnachrichtendienst (BND) cooperate with their US counterparts as a "third party" government through the Fourteen Eyes agreement, Washington spooks still feel the need to constantly spy on Berlin.
The 2013 Snowden leaks
revealed that Germany is a major target of US espionage run out of
the NSA's own European Cryptologic Center (ECC), known
affectionately as the "Dagger Complex," located in Griesheim, in the
German state of Hesse.
The documents also note
that the NSA uses its infamous XKEYSCORE software to trawl up its
main areas of interest from inside the German government, namely
foreign policy, economic stability, new technologies, advanced
weaponry, arms exports, and international trade.
Hayden lamented the German disclosure but admitted the US government had grossly underestimated German values on issues pertaining to privacy, stating:
In similar fashion, both the European Union and the United Nations are also said to be under US surveillance.
Like with Germany, NSA espionage objectives on the EU include foreign policy goals, the economy, international trade, and "energy security."
The targeting of the UN adds a whole other international dimension to these operations.
A 2013 report filed by The Guardian newspaper paints a rather disturbing picture:
To help answer that question, we need to go back 50 years and look at what happened in Australia circa 1970.
www.roninfilms.com.au/feature/9916/allies.html
Revelations included an admission by Victor Marchetti, former executive assistant to the deputy director of the CIA (1955-1969), who stated:
Some officials testified
that their loyalty was not to their elected leaders but the CIA.
For the Americans, managing this autonomous power structure first meant securing its geostrategic interests in host countries as well as its strategic facilities like the NSA's Pine Gap listening base located in central Australia.
Securing these assets
became a national security issue - Washington could not risk any
newly elected government interfering with US intelligence
operations.
While the notorious Petrov Affair (1954) helped sideline Australia's Labor party for many years afterwards, the real trigger for a US-backed coup came in 1972 when Gough Whitlam led Labor to victory for the first time in 23 years.
The Whitlam government called into question Australia's supporting roles in various military conflicts taking place in Southeast Asia, including Vietnam and Indonesia, and challenged the top-secret nature of US bases operating in Australia.
Details of a CIA plot to depose Whitlam were revealed by NSA contractor Christopher Boyce, who was convicted of espionage and sentenced to federal prison in the US.
Boyce's story was later
made into a cinematic classic, The Falcon and the Snowman.
In the case of Australia, this meant US intervention to derail any government that might threaten US foreign policy and its global intelligence operations.
From this vignette, one could draw a parallel to Washington's ill-treatment of Germany - another ally that also hosts numerous US military bases and intelligence-gathering facilities, and which functions as an anchor for US operations in Europe in much the same way Australia does for the Asia-Pacific region.
The China Syndrome
Firms like,
...command near-global monopolies in their respective markets.
This means that as long
as those Western firms permeate and dominate the planetary
information space, Five Eyes operatives only require a backdoor into
a handful of these firms to surveil and control almost every aspect
of public (and even private) life.
That includes keeping out
any foreign product which could cause a wrinkle in their control
matrix. As expected, this situation feeds neatly into a ready-made
geopolitical drama, especially if the Trojan Horse in question
arrives in the form of a Chinese firm.
To make this project work, the UK has to partner with the only company who can deliver enough advanced equipment on time and on budget:
In theory, Five Eyes fears may be warranted.
With 5G set to provide the new framework for real-time spying and data monitoring, Western spy chiefs and politicians are afraid of becoming too reliant on potential geopolitical and commercial rival China.
Practically speaking, Huawei's hardware is fairly standardized and compatible with other components used to configure the UK's new 5G network, and to date, there is no proof of any latent Chinese spyware in any of the components in question.
UK spy chiefs are already lining up in defence of the realm, with former MI6 head Richard Dearlove chiming in:
A number of tertiary arguments against Huawei are being employed by Western officials including charges that China steals Western intellectual property, or that Chinese firms are inherently 'anti-competitive' because of state subsidies given to many enterprises.
Reading between the lines, more of a worry for the Five Eyes (or a privatized Spectre syndicate) is the fact that a whole range of other Huawei products could employ a different proprietary Chinese encryption protocol that would give not only Chinese officials and intelligence workers a privacy edge, but the public mass-consumer too - keeping the NSA from intercepting a user's communications, or at least making it much more difficult.
Thus, keeping Chinese
products out of Western surveillance zones could be a major priority
for Five Eyes technocrats.
Huawei Chairman Liang
Hua responded at an industry press conference during the
China-Germany-USA Media Forum, saying that the US placing Huawei on
its entity list has had "no substantial impact" on Huawei's business
and that all of the company's flagship products are shipping as
normal.
In this war, the winning
edge might be with the state-managed economy where Chinese planners
typically plot the course ahead looking at 20 to 30-year windows, as
opposed to US firms that prioritize mere quarterly gains and
shareholder dividends.
Naturally, this poses a direct threat to the West's global digital media and communications mafia, and its overlapping fraternal network of government agencies, corporations and 'white-collar' organized criminal syndicates.
On this point, there is
little advice one can offer other than to stay off social media or
go 'off-grid' (offline) as much as possible to avoid leaving a
detailed digital footprint that can be used to build a profile on
you.
Besides using a reliable encrypted chat or messaging service, if you are not already using a Virtual Private Network (VPN), then now may be a good time to start.
VPN encrypts all of your internet traffic and scrambles your IP address, making it difficult for anyone monitoring you online to pinpoint your identity, device, and physical location.
One key requirement is trying to use a service based outside the Fourteen Eyes countries.
This means you may not be immediately exposed should your service provider's host country ask for back door access to your internet records. If you are using a service within the Fourteen, then be sure to choose a company that has a 'no logs' policy...
In other words, should a US or UK agency like the NSA or GCHQ make a formal request from a service provider to hand over all your internet search data, then there will be nothing they can hand over.
Likewise, you can use a
number of encrypted instant messaging services like Telegram, or
encrypted email services like
Proton Mail, and also consider using
an internet browser that doesn't keep data on your surfing like Brave, or a search engine like
Duck Duck Go which doesn't save data
on all of your search activity.
This means only the sender and receiver can view the content, concealing communications from the prying eyes of Western spy agencies.
Needless to say, insatiable state authoritarians are not happy about this and have laid down a harrowing ultimatum to tech companies, demanding write-in backdoor access protocols supposedly for "law enforcement."
If firms do not comply, government officials threaten they should be ready for brute force intrusions by agents of the state.
Knowing they do not have
the public on their side, governments have resorted to intimidation
and scare tactics in order to swing public opinion in their favor.
The bill requires that
any "communications service provider" (ISPs, social media platforms,
VOIP, email providers and messaging service) must comply with a
secret warrant signed by the Home Secretary which names any persons
or organizations the government wishes to spy on.
According to researchers, the draconian decree, also known as the 'Snooper's Charter', requires tech companies to insert special malware onto their systems so the spooks can use their platforms to,
The secret warrant explicitly allows those companies to violate any other laws in complying with the warrant.
Essentially, the warrant enables said tech firms to violate the law in the process of complying with the government's secret snooper's warrant.
This would also include
the Home Secretary ordering firms like Facebook, Samsung or Apple to
quietly remove their 'secure communication' features from products
without notifying the public about it.
Danny O'Brien from EFF noted how the UK government has been very careful not to pin itself down with any specifics, explaining,
EFF describes the severity of the IPA in terms of riding roughshod over basic civil rights and protections:
IPA provisions might also
include the government forcing a chain of coffee shops to use the
company's free WiFi service to deploy British spy agency malware
against its customers.
This is a shocking act of
overreach by the British state - one that exceeds even the most
invasive state intervention in a country like China.
While there is considerable push-back from tech companies and public advocacy groups, there's surprisingly little rebellion from most mainline politicians, partly because they are not being pressured from their constituents on this issue.
What anti-privacy initiatives like the IPA clearly demonstrate is that Britain is the one clearly setting the dark tone and aggressive pace for the Five Eyes cohort. The agenda clearly seeks a renewed license to put tech firms in a corner by deploying emotive language and invoking evermore dramatic conspiracy claims.
In her article written for The Telegraph, current UK Home Secretary Priti Patel even went so far as to equate Facebook's noncompliance with aiding and abetting,
Of course, Patel's comments shouldn't surprise anyone who has followed the issue of privacy over the years, particularly in the post-9/11 era where politicians and national security state operatives routinely gaslight the public to justify every intrusion or roll-back of privacy rights by citing the most extreme and infrequent instances of 'terrorism'.
For the 21st
century technocracy and police state, that's been the gift that just
keeps giving, but by the same token the public have become
increasingly wary of such dramatic government claims due to the fact
that very rarely, if ever, has government wiretapping or backdoor
spying actually thwarted a terrorist attack in what is popularly
referred to in national security rhetoric and Hollywood propaganda
lore as 'the ticking bomb' scenario.
Five Eyes member Australia took the matter even further, threatening to "break in" if tech companies do not facilitate the access requirements of the state.
This new policy initiative was expressed unabashedly in a memo issued by the Australian Dept of Home Affairs on behalf of the Five Eyes alliance:
A closer look at the memo reveals that Australia's authoritarian designs are not restricted to stopping terrorists and pedophiles but appear to target any entities they feel are "sowing discord" (including any popular dissenting opinion and analysis), that supposedly threatens our vaunted "democratic institutions."
This may also include any foreign media (as depicted in the heavily promoted 'Russian disinformation' narrative), independent media, and free-thinking individuals on social media.
The language could not be more arbitrary:
This, alongside Britain's notorious 'Snooper's Charter', demonstrates how Five Eyes partners are working in concert by gradually laying down an alliance-wide legal framework that will legitimize what would normally be unwarranted activity by state agencies.
This is done by
suspending any constitutional provisions or rights - all in the name
of protecting national security, or even the national interest as
the state defines it.
For the moment, this technology offers fairly robust protection from the prying eyes of the intelligence services, but advances in computing power may eventually put many of these protections at grave risk.
New advances in quantum computing threaten to usher in a new event horizon whereby the next generation of computers could conceivably crack today's industry-standard 256-bit encryption key in a relatively short period of time - in mere minutes, or even seconds.
Researchers at the Massachusetts Institute of Technology (MIT) have shown how a quantum processor can crack a seemingly impenetrable 2,048-bit RSA encryption in only eight hours.
Exactly how far off we are to this quantum revolution is anyone's guess but when it arrives it could tip the scales of privacy away from the consumer and in favor of those organizations who control this new technology, namely Silicon Valley monopolists and the intergovernmental Five Eyes complex.
On the flip side,
advances in quantum decryption may also coincide with new methods of
encryption that could slow down quantum crackers enough to make
decryption impractical.
Our future depends on
it...
|